microsoft
Infrequently Poster

Credit 3
Totalpost 1
Registered 2008-10-28
|  #1 Our Micropoint protect us against Microsoft Security Hole-MS08067 #1 Our Micropoint protect us against Microsoft Security Hole-MS08067

NOTICE: October 23, 2008: Today the MSRC released Security Bulletin MS08-067. For more information on this bulletin, and to stay protected get the latest information from the MMPC here on our blog: http://blogs.technet.com/mmpc/ar ... -protected-now.aspx
Get Protected, Now!
Thursday, October 23, 2008 10:00 AM by mmpc
Microsoft released a security update today that fixes a vulnerability that affects all supported versions of Windows. On some versions of Windows, an unauthenticated attacker can remotely execute code on a vulnerable computer. Basically if file sharing is enabled and the security update is not installed yet, the computer is vulnerable. File sharing is enabled in several scenarios though it is disabled by default in XP SP2 and newer operating systems. See the "Security Vulnerability Research & Defense" blog for further information. Security Bulletin MS08-067 also provides more details. Microsoft strongly recommends that you update your computer(s) immediately.
We are already seeing a small number of attacks using this vulnerability. The situation can change now that the security update is public. We have seen cases in the past where information on how to exploit a newly updated vulnerability was posted to the web only a few days, or even hours, after a security update is released. Did we already mention that we recommend you quickly install the security update?
We have detection for the current attacks. Its name is Exploit:Win32/MS08067.gen!A and it is included in VDM update version 1.45.1012.0 and higher. We released these VDMs this morning shortly after 10 AM PDT. These current attacks will be detected when the attack file is copied to the victim’s computer, for example, as part of its self replication. Note that we are not aware of any self replicating malware that is exploiting this vulnerability at the moment. This update can detect the current attacks and we will continue to update should more be created. Our team, the Microsoft Malware Protection Center, is on the alert and is closely monitoring the situation.
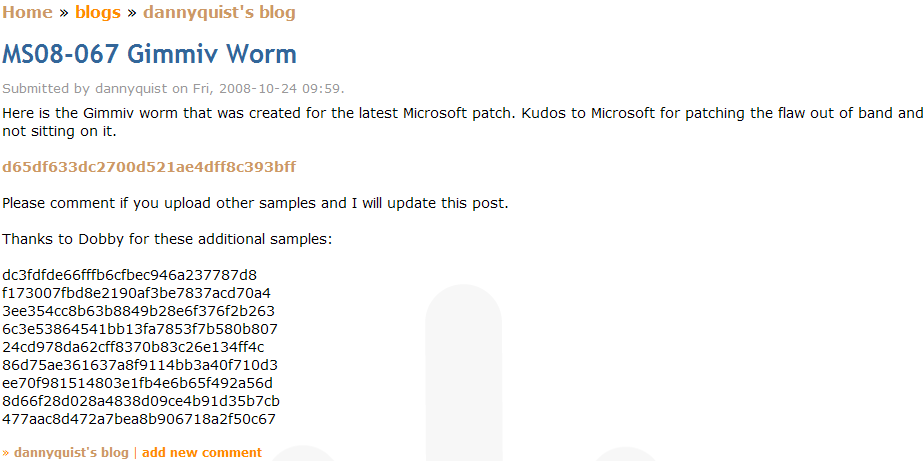
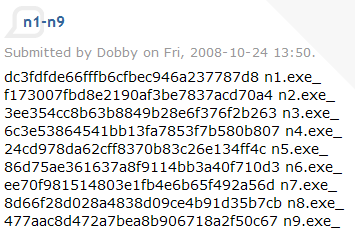
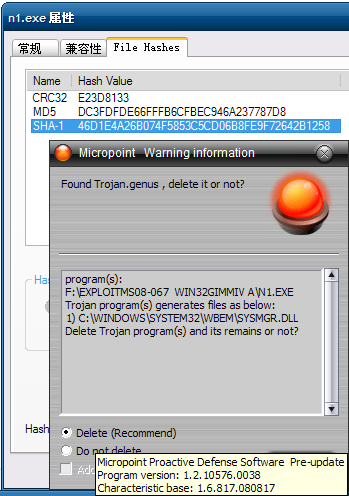
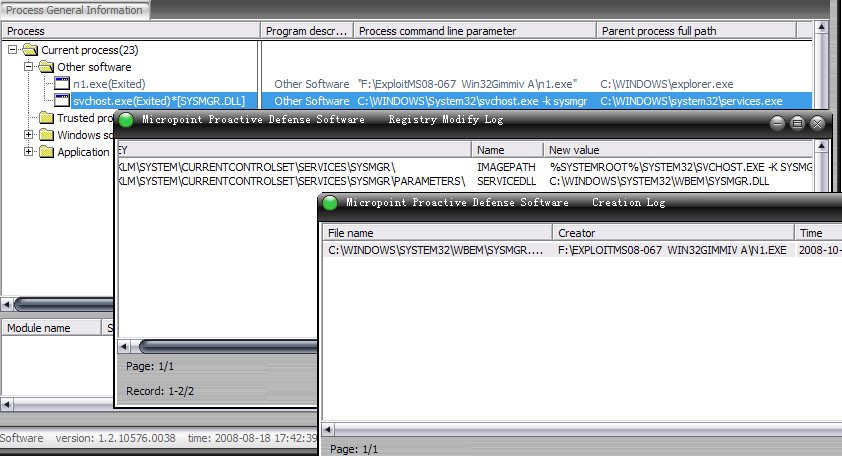
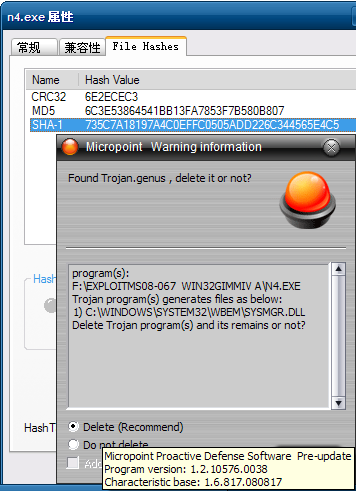
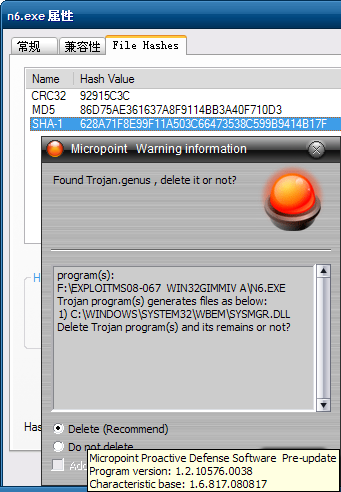
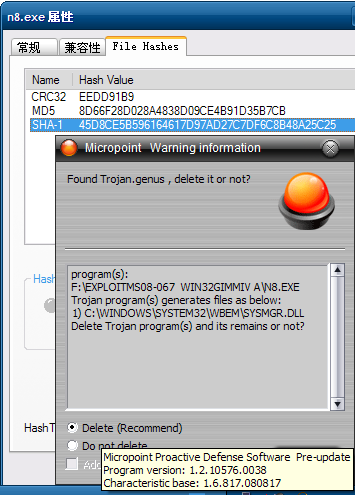
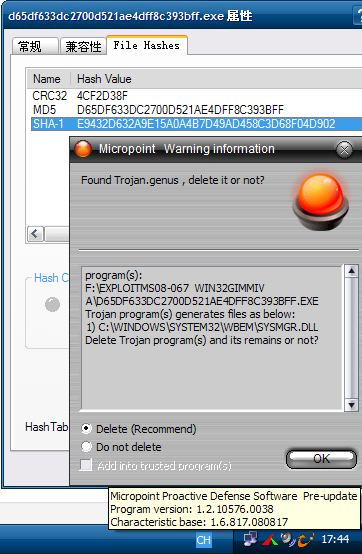
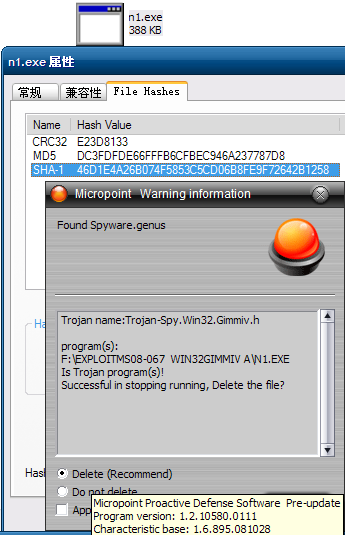
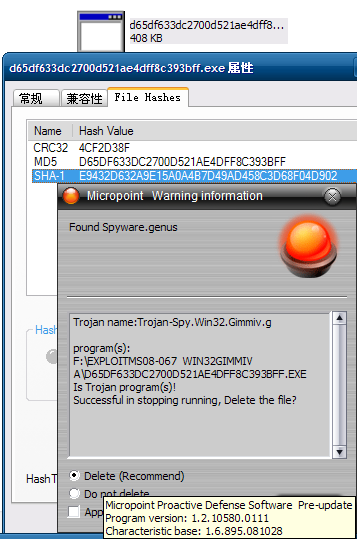
Currently, attacks try to download a trojan named n2.exe to the victim’s computer and there are now two different versions of this binary. Our products are able to detect both files as TrojanSpy:Win32/Gimmiv.A. This trojan drops another DLL that we detect as TrojanSpy:Win32/Gimmiv.A.dll. The malware deletes itself after it executes so you may not find it even on systems that were previously infected. Our products provide real-time protection that will block that malware from being copied to the hard drive. You can read more details about this malware in our encyclopedia write ups.
Windows Live OneCare safety scanner, Windows Live OneCare and the various Forefront products include these detections. If you believe that you identified new malware that is exploiting this vulnerability, or other malware, please let us know by submitting that file to our portal.
So get protected, and the sooner, the better.
Ziv Mador
Microsoft Malware Protection Center:
:http://blogs.technet.com/mmpc/ar ... -protected-now.aspx


Summary
Exploit:Win32/MS08067.gen!A is a generic detection for code that attempts to exploit a vulnerability in SVCHOST.EXE. If the vulnerability is successfully exploited, it could allow remote code execution when file sharing is enabled.
On targeted hosts running Windows 2003, XP, 2000 or NT, this remote attack may be performed by an unauthenticated user. Successful exploitation of the vulnerability on systems with default installations of Windows Vista and Windows Server 2008 require authentication due to protections introduced as part of user access control (UAC) that enforce additional levels of integrity.
Microsoft strongly recommends that users apply the update referred to in Security Bulletin MS08-067 immediately.
Symptoms
There are no common symptoms associated with this threat. Alert notifications from installed antivirus software may be the only symptom(s).
 
 

|
|