本帖最后由 极限度—魔 于 2012-12-2 12:19 编辑
说是亿家,但是它加密了广告地址,用OD或者winhex搜索 51pc114.cn,然后填充掉地址后,是无法去除的,还是会有广告弹出.
用 E-Debug Events 打开软件,然后选择 Open -- 选择需要打开的软件--按 Start,然后它会出现
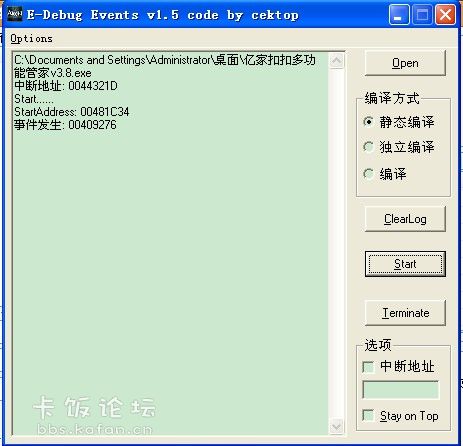 ===========================我是分割线=================================
===========================我是分割线=================================
载入OD--组合键 Ctrl+G--输入 00409276--F2断下--再就是F9了
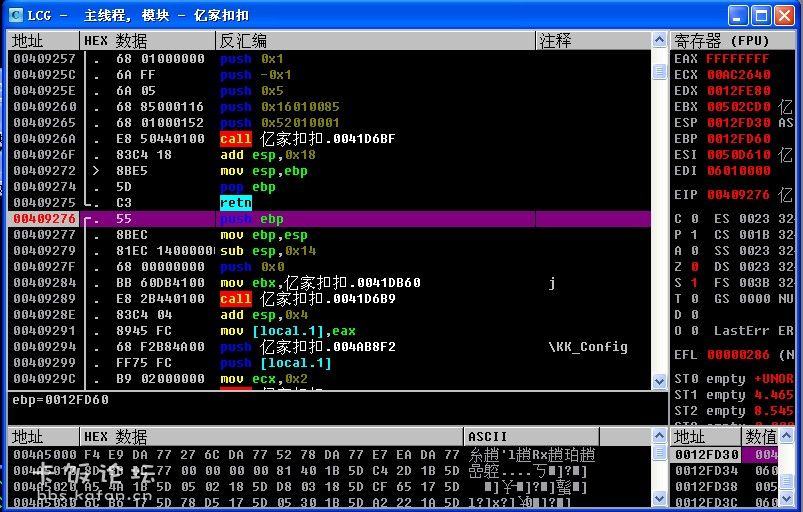
接下来我们就F8单步走--一直走,走到数据框出现了网站后就停下〖PS:需要走N久,可以一直按住 F8〗,当走到 a90~opqr!@#$%^&*bcdefghtuvwhijklmnxyz12345678()_+-= 这里后就要慢慢按了
〖PS:当然,伱也可以搜索这个字符串,然后断点.再F9运行,只不过不会的人都不会找,我也不会 这个就是加密地址了〗 这个就是加密地址了〗
前面说了,这个是加密地址,接下来我们的然后就是解密喇.
在这里要慢慢得按F8了.一直按--按到数据框出现了网站后就停下
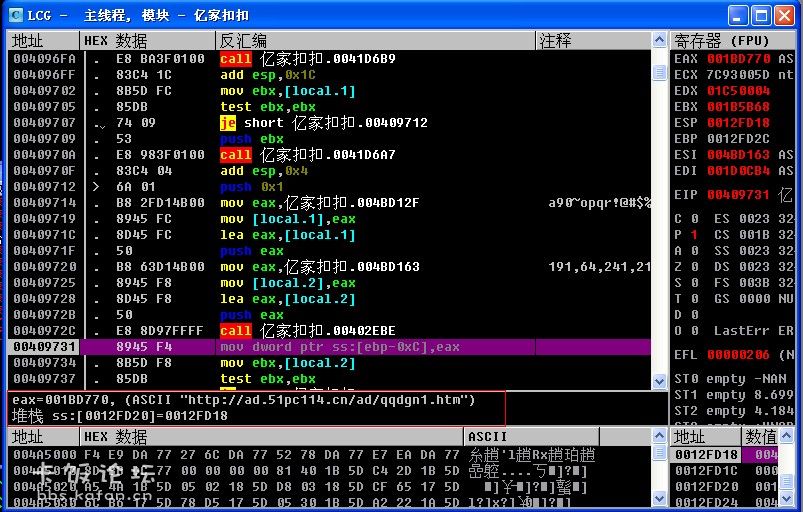
- 00409709 |. 53 push ebx
- 0040970A |. E8 983F0100 call 亿家扣扣.0041D6A7
- 0040970F |. 83C4 04 add esp,0x4
- 00409712 |> 6A 01 push 0x1
- 00409714 |. B8 2FD14B00 mov eax,亿家扣扣.004BD12F ; a90~opqr!@#$%^&*bcdefghtuvwhijklmnxyz12345678()_+-=
- 00409719 |. 8945 FC mov [local.1],eax
- 0040971C |. 8D45 FC lea eax,[local.1]
- 0040971F |. 50 push eax
- 00409720 |. B8 63D14B00 mov eax,亿家扣扣.004BD163 ; 191,64,241,211,107,191,14,44,190,229,49,132,236,190,106,149,178,191,112,197,166,242,116,197,226,191,38,154,249,240,33,219,167,224,33,147,184,160,107,156,162,252
- 00409725 |. 8945 F8 mov [local.2],eax
- 00409728 |. 8D45 F8 lea eax,[local.2]
- 0040972B |. 50 push eax
- 0040972C |. E8 8D97FFFF call 亿家扣扣.00402EBE
- 00409731 8945 F4 mov dword ptr ss:[ebp-0xC],eax ; // Nop
这里只是打开后的广告,还有一个是退出后的弹窗广告,填充后我们继续F8
===========================我是分割线=================================
方法还是和上面的一样.F8走到这里后用Nop填充就完成了- 00409734 |. 8B5D F8 mov ebx,[local.2]
- 00409737 |. 85DB test ebx,ebx
- 00409739 |. 74 09 je short 亿家扣扣.00409744
- 0040973B |. 53 push ebx
- 0040973C |. E8 663F0100 call 亿家扣扣.0041D6A7
- 00409741 |. 83C4 04 add esp,0x4
- 00409744 |> 8B5D FC mov ebx,[local.1]
- 00409747 |. 85DB test ebx,ebx
- 00409749 |. 74 09 je short 亿家扣扣.00409754
- 0040974B |. 53 push ebx
- 0040974C |. E8 563F0100 call 亿家扣扣.0041D6A7
- 00409751 |. 83C4 04 add esp,0x4
- 00409754 |> 6A 00 push 0x0
- 00409756 |. FF75 F4 push [local.3]
- 00409759 |. 6A FF push -0x1
- 0040975B |. 6A 0B push 0xB
- 0040975D |. 68 85080116 push 0x16010885
- 00409762 |. 68 01000152 push 0x52010001
- 00409767 |. E8 533F0100 call 亿家扣扣.0041D6BF
- 0040976C |. 83C4 18 add esp,0x18
- 0040976F |. 8B5D F4 mov ebx,[local.3]
- 00409772 |. 85DB test ebx,ebx
- 00409774 |. 74 09 je short 亿家扣扣.0040977F
- 00409776 |. 53 push ebx
- 00409777 |. E8 2B3F0100 call 亿家扣扣.0041D6A7
- 0040977C |. 83C4 04 add esp,0x4
- 0040977F |> 6A 01 push 0x1
- 00409781 |. B8 04D24B00 mov eax,亿家扣扣.004BD204 ; 12345678()_+-=a90~opqr!@#$%^&*bcdefghtuvwhijklmnxyz
- 00409786 |. 8945 FC mov [local.1],eax
- 00409789 |. 8D45 FC lea eax,[local.1]
- 0040978C |. 50 push eax
- 0040978D |. B8 38D24B00 mov eax,亿家扣扣.004BD238 ; 191,222,111,77,245,33,144,178,32,123,175,26,114,32,244,11,44,33,238,91,56,108,234,91,124,33,184,4,103,110,191,69,57,126,191,13,38,61,245,2,60,98
- 00409792 |. 8945 F8 mov [local.2],eax
- 00409795 |. 8D45 F8 lea eax,[local.2]
- 00409798 |. 50 push eax
- 00409799 |. E8 2097FFFF call 亿家扣扣.00402EBE
- 0040979E 8945 F4 mov dword ptr ss:[ebp-0xC],eax ; // Nop
后记:其实也就是说,走到了那里后,数据框出现了广告地址后,说明地址已经解密了. |