本帖最后由 Jerry.Lin 于 2020-4-10 00:27 编辑
HitmanPro Alert 拦截
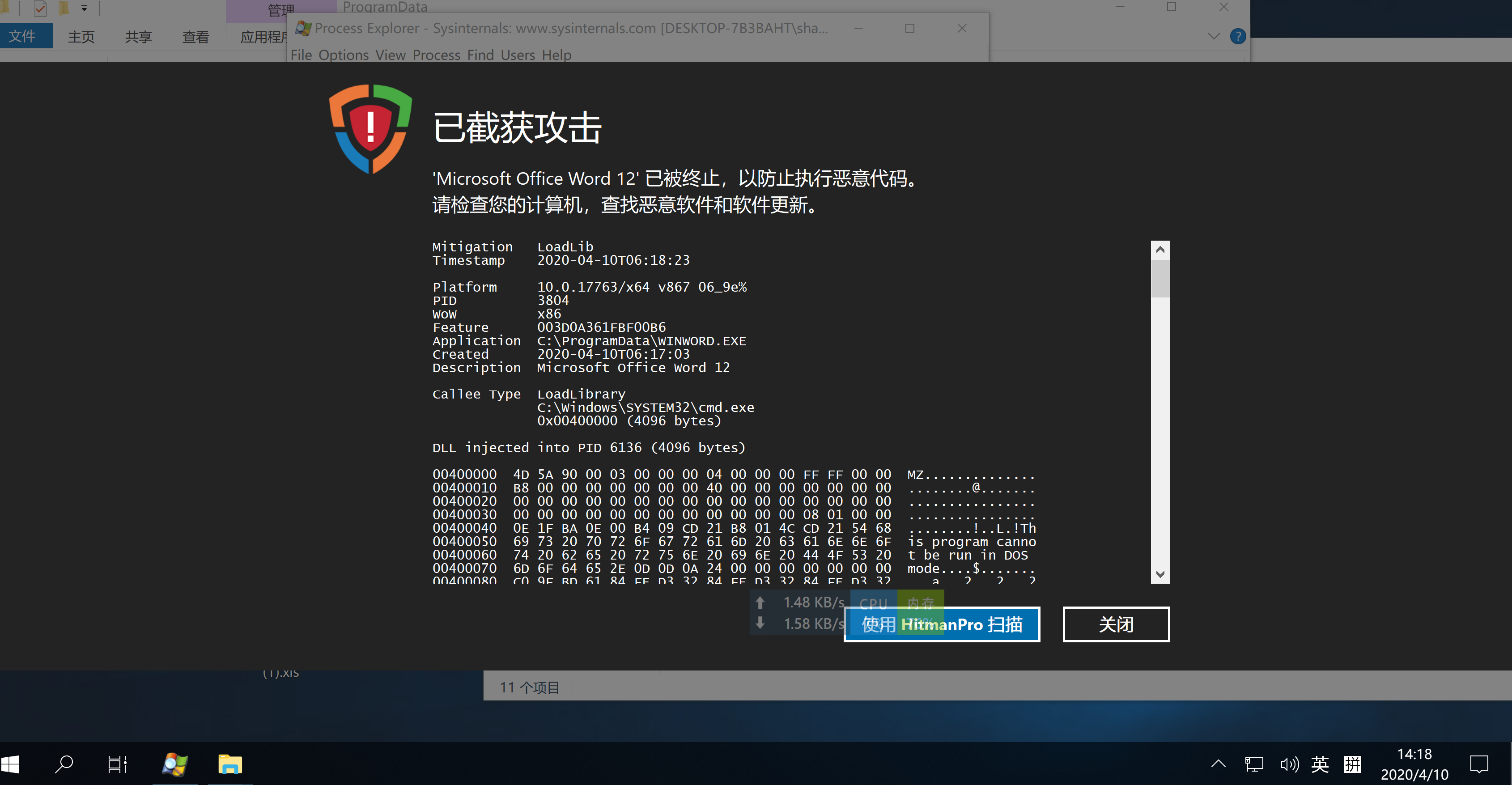
- Mitigation LoadLib
- Timestamp 2020-04-10T06:19:55
- Platform 10.0.17763/x64 v867 06_9e%
- PID 4208
- WoW x86
- Feature 003D0A361FBF00B6
- Application C:\ProgramData\WINWORD.EXE
- Created 2020-04-10T06:17:03
- Description Microsoft Office Word 12
- Callee Type LoadLibrary
- C:\Windows\SYSTEM32\svchost.exe
- 0x00400000 (4096 bytes)
- DLL injected into PID 924 (4096 bytes)
- 00400000 4D 5A 90 00 03 00 00 00 04 00 00 00 FF FF 00 00 MZ..............
- 00400010 B8 00 00 00 00 00 00 00 40 00 00 00 00 00 00 00 ........@.......
- 00400020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
- 00400030 00 00 00 00 00 00 00 00 00 00 00 00 08 01 00 00 ................
- 00400040 0E 1F BA 0E 00 B4 09 CD 21 B8 01 4C CD 21 54 68 ........!..L.!Th
- 00400050 69 73 20 70 72 6F 67 72 61 6D 20 63 61 6E 6E 6F is program canno
- 00400060 74 20 62 65 20 72 75 6E 20 69 6E 20 44 4F 53 20 t be run in DOS
- 00400070 6D 6F 64 65 2E 0D 0D 0A 24 00 00 00 00 00 00 00 mode....$.......
- 00400080 C0 9F BD 61 84 FE D3 32 84 FE D3 32 84 FE D3 32 ...a...2...2...2
- 00400090 07 E2 DD 32 AF FE D3 32 FF E2 DF 32 87 FE D3 32 ...2...2...2...2
- 004000A0 D2 E1 C0 32 A8 FE D3 32 E6 E1 C0 32 91 FE D3 32 ...2...2...2...2
- 004000B0 84 FE D2 32 D0 FC D3 32 B2 D8 D8 32 E2 FE D3 32 ...2...2...2...2
- 004000C0 B2 D8 D9 32 54 FE D3 32 6C E1 D8 32 C8 FE D3 32 ...2T..2l..2...2
- 004000D0 6C E1 D9 32 9F FE D3 32 84 FE D3 32 9B FE D3 32 l..2...2...2...2
- 004000E0 43 F8 D5 32 85 FE D3 32 52 69 63 68 84 FE D3 32 C..2...2Rich...2
- 004000F0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
- 00400100 00 00 00 00 00 00 00 00 50 45 00 00 4C 01 04 00 ........PE..L...
- 00400110 73 7C 83 5E 00 00 00 00 00 00 00 00 E0 00 0F 01 s|.^............
- 00400120 0B 01 06 00 00 50 0A 00 00 F0 7B 00 00 00 00 00 .....P....{.....
- 00400130 15 66 08 00 00 10 00 00 00 60 0A 00 00 00 40 00 .f.......`....@.
- 00400140 00 10 00 00 00 10 00 00 04 00 00 00 00 00 00 00 ................
- 00400150 04 00 00 00 00 00 00 00 00 50 86 00 00 10 00 00 .........P......
- 00400160 00 00 00 00 02 00 00 00 00 00 10 00 00 10 00 00 ................
- 00400170 00 00 10 00 00 10 00 00 00 00 00 00 10 00 00 00 ................
- Stack Trace
- # Address Module Location
- -- -------- ------------------------ ----------------------------------------
- 1 7718BDCF KernelBase.dll LoadLibraryExW +0x14f
- 2 77189E51 KernelBase.dll LoadLibraryW +0x11
- 3 2FAE1582 WINWORD.EXE
- 4 2FAE155D WINWORD.EXE
- 5 76B5FE09 kernel32.dll BaseThreadInitThunk +0x19
- 6 7756607D ntdll.dll RtlGetAppContainerNamedObjectPath +0xed
- 7 7756604D ntdll.dll RtlGetAppContainerNamedObjectPath +0xbd
- 8 02CE22E0 wwlib.dll
- 685482c1ad PUSH DWORD 0xadc18254
- e8ddc71e00 CALL 0x2eceac7
- 6932f41ef2f5 IMUL ESI, [EDX], 0xf5f21ef4
- 6c INS BYTE [ES:EDI], DX
- 1d6189a8bb SBB EAX, 0xbba88961
- e31e JECXZ 0x2ce2316
- Loaded Modules (63)
- -----------------------------------------------------------------------------
- 2FAE0000-2FB37000 WINWORD.EXE (Microsoft Corporation),
- version: 12.0.4518.1014
- ...
- 02BA0000-03576000 wwlib.dll (),
- version:
- 74970000-7497F000 WTSAPI32.dll (Microsoft Corporation),
- version: 10.0.17763.1 (WinBuild.160101.0800)
- Process Trace
- 1 C:\ProgramData\WINWORD.EXE [4208] 2020-04-10T06:19:54
- 2 C:\Windows\explorer.exe [3720] 2020-04-10T06:14:42
- 3 C:\Windows\System32\userinit.exe [3632] 2020-04-10T06:14:41 23.9s
- 4 C:\Windows\System32\winlogon.exe [676] 2020-04-10T06:14:18
- winlogon.exe
- 5 C:\Windows\System32\smss.exe [516] 2020-04-10T06:14:17 569ms
- \SystemRoot\System32\smss.exe 000000ac 00000088
- 6 C:\Windows\System32\smss.exe [352] 2020-04-10T06:14:09
- \SystemRoot\System32\smss.exe
- Dropped Files
- Thumbprints
- ad3aeb9fe782257b1395f950bc1e4547582ada319b3dd190b5f73223ac0909d9
放行此次漏洞拦截,触发反勒索模块
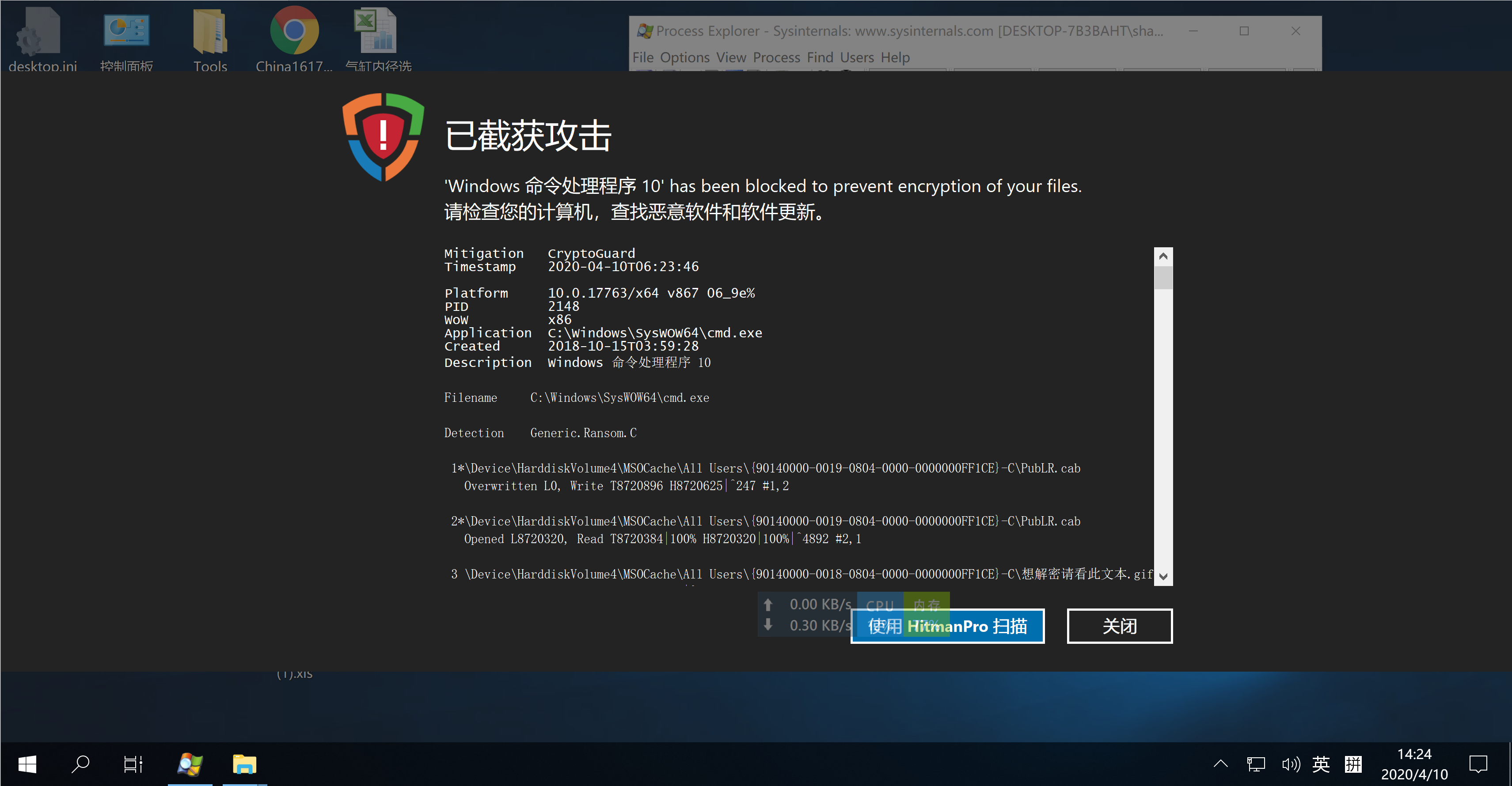
- Mitigation CryptoGuard
- Timestamp 2020-04-10T06:23:46
- Platform 10.0.17763/x64 v867 06_9e%
- PID 2148
- WoW x86
- Application C:\Windows\SysWOW64\cmd.exe
- Created 2018-10-15T03:59:28
- Description Windows 命令处理程序 10
- Filename C:\Windows\SysWOW64\cmd.exe
- Detection Generic.Ransom.C
- 1*\Device\HarddiskVolume4\MSOCache\All Users\{90140000-0019-0804-0000-0000000FF1CE}-C\PubLR.cab
- Overwritten L0, Write T8720896 H8720625|^247 #1,2
- 2*\Device\HarddiskVolume4\MSOCache\All Users\{90140000-0019-0804-0000-0000000FF1CE}-C\PubLR.cab
- Opened L8720320, Read T8720384|100% H8720320|100%|^4892 #2,1
- 3 \Device\HarddiskVolume4\MSOCache\All Users\{90140000-0018-0804-0000-0000000FF1CE}-C\想解密请看此文本.gif
- Created L0, Write T259584 H259540|^10783 #3
- 4 \Device\HarddiskVolume4\MSOCache\All Users\{90140000-0018-0804-0000-0000000FF1CE}-C\想解密请看此文本.txt
- Created L0, Write T2560 H2475|^9397 #4
- 5 \Device\HarddiskVolume4\MSOCache\All Users\{90140000-0018-0804-0000-0000000FF1CE}-C\PptLR.cab
- Opened, Deleted L42220154 #5
- 6 \Device\HarddiskVolume4\MSOCache\All Users\{90140000-0018-0804-0000-0000000FF1CE}-C\PptLR.cab.WannaRen
- Created L0, Write T42220544 H42220154|^219 #6
- 7 \Device\HarddiskVolume4\MSOCache\All Users\{90140000-0018-0804-0000-0000000FF1CE}-C\PptLR.cab
- Overwritten L0, Write T42220544 H42220154|^219 #7
- ...
- 41*\Device\HarddiskVolume4\MSOCache\All Users\{90140000-0011-0000-0000-0000000FF1CE}-C\OWOW64WW.cab
- Overwritten L0, Write T23865856 H23865705|^281 #42,43
- 42*\Device\HarddiskVolume4\MSOCache\All Users\{90140000-0011-0000-0000-0000000FF1CE}-C\OWOW64WW.cab
- Opened L23865400, Read T23865856|100% H23865400|100%|^3142 #43,42
- Loaded Modules (48)
- -----------------------------------------------------------------------------
- 00400000-00C65000 cmd.exe (Microsoft Corporation),
- Version: 10.0.17763.1
- ...
- 74AB0000-74AD3000 USERENV.dll (Microsoft Corporation),
- Version: 10.0.17763.1
- Code Injection
- 00401000-004A6000 660KB C:\ProgramData\WINWORD.EXE [6020]
- 1 C:\ProgramData\WINWORD.EXE [6020] 2020-04-10T06:23:19 1.4s
- 2 C:\Windows\explorer.exe [3720] 2020-04-10T06:14:42
- 3 C:\Windows\System32\userinit.exe [3632] 2020-04-10T06:14:41 23.9s
- 4 C:\Windows\System32\winlogon.exe [676] 2020-04-10T06:14:18
- winlogon.exe
- 5 C:\Windows\System32\smss.exe [516] 2020-04-10T06:14:17 569ms
- \SystemRoot\System32\smss.exe 000000ac 00000088
- 6 C:\Windows\System32\smss.exe [352] 2020-04-10T06:14:09
- \SystemRoot\System32\smss.exe
- Process Trace
- 1 C:\Windows\SysWOW64\cmd.exe [2148] 2020-04-10T06:23:20
- cmd.exe
- 2 C:\ProgramData\WINWORD.EXE [6020] 2020-04-10T06:23:19 1.4s
- 3 C:\Windows\explorer.exe [3720] 2020-04-10T06:14:42
- 4 C:\Windows\System32\userinit.exe [3632] 2020-04-10T06:14:41 23.9s
- 5 C:\Windows\System32\winlogon.exe [676] 2020-04-10T06:14:18
- winlogon.exe
- 6 C:\Windows\System32\smss.exe [516] 2020-04-10T06:14:17 569ms
- \SystemRoot\System32\smss.exe 000000ac 00000088
- 7 C:\Windows\System32\smss.exe [352] 2020-04-10T06:14:09
- \SystemRoot\System32\smss.exe
- Dropped Files
- 1 C:\@WannaRen@.exe
- Dropped by \Device\HarddiskVolume4\Windows\SysWOW64\cmd.exe [2148]
- 2 C:\æƒ3解åˉ†èˉ·çœ‹æ-¤æ–‡æœ¬.txt
- Dropped by \Device\HarddiskVolume4\Windows\SysWOW64\cmd.exe [2148]
- 3 C:\MSOCache\All Users\{90140000-0011-0000-0000-0000000FF1CE}-C\OWOW64WW.cab
- Dropped by \Device\HarddiskVolume4\Windows\SysWOW64\cmd.exe [2148]
- 4 C:\MSOCache\All Users\{90140000-0011-0000-0000-0000000FF1CE}-C\OWOW64WW.cab.WannaRen
- Dropped by \Device\HarddiskVolume4\Windows\SysWOW64\cmd.exe [2148]
- 5 C:\MSOCache\All Users\{90140000-0011-0000-0000-0000000FF1CE}-C\æƒ3解åˉ†èˉ·çœ‹æ-¤æ–‡æœ¬.txt
- Dropped by \Device\HarddiskVolume4\Windows\SysWOW64\cmd.exe [2148]
- 6 C:\MSOCache\All Users\{90140000-0011-0000-0000-0000000FF1CE}-C\æƒ3解åˉ†èˉ·çœ‹æ-¤æ–‡æœ¬.gif
- Dropped by \Device\HarddiskVolume4\Windows\SysWOW64\cmd.exe [2148]
- ...
- 19 C:\MSOCache\All Users\{90140000-0019-0804-0000-0000000FF1CE}-C\PubLR.cab
- Dropped by \Device\HarddiskVolume4\Windows\SysWOW64\cmd.exe [2148]
- Thumbprints
- 4936f22d3d39bef09ef743be636de2a417f1c4aa9c48dd0ed497fb4cdecb4aa6
|
 [复制链接]
[复制链接]