本帖最后由 85683213 于 2020-4-25 17:43 编辑
https://attackevals.mitre.org/APT29/
Participants:
Bitdefender, CrowdStrike, Cybereason,
CyCraft, Blackberry Cylance, Elastic,
F-Secure, FireEye, GoSecure,
HanSight, Kaspersky, Malwarebytes,
McAfee, Microsoft, Palo Alto Networks,
ReaQta, Secureworks, SentinelOne,
Symantec, Trend Micro, VMware Carbon Black
Scenario Overview:

Two scenarios emulate publicly reported APT29/Cozy Bear/The Dukes/YTTRIUM tradecraft and operational flows. The first scenario (executed with Pupy, Meterpreter, and custom tooling) begins with the execution of a payload delivered by a widespread "spray and pray" spearphishing campaign, followed by a rapid "smash and grab" collection and exfiltration of specific file types. After completing the initial data theft, the value of the target is realized, and the adversary drops a secondary, stealthier toolkit used to further explore and compromise the target network.
The second scenario (executed with PoshC2 and custom tooling) focuses on a very targeted and methodical breach, beginning with the execution of a specially crafted payload designed to scrutinize the target environment before executing. The scenario continues through a low and slow takeover of the initial target and eventually the entire domain. Both scenarios include executing previously established persistence mechanisms after a simulated time lapse to further the scope of the breach.
Detection Categories:
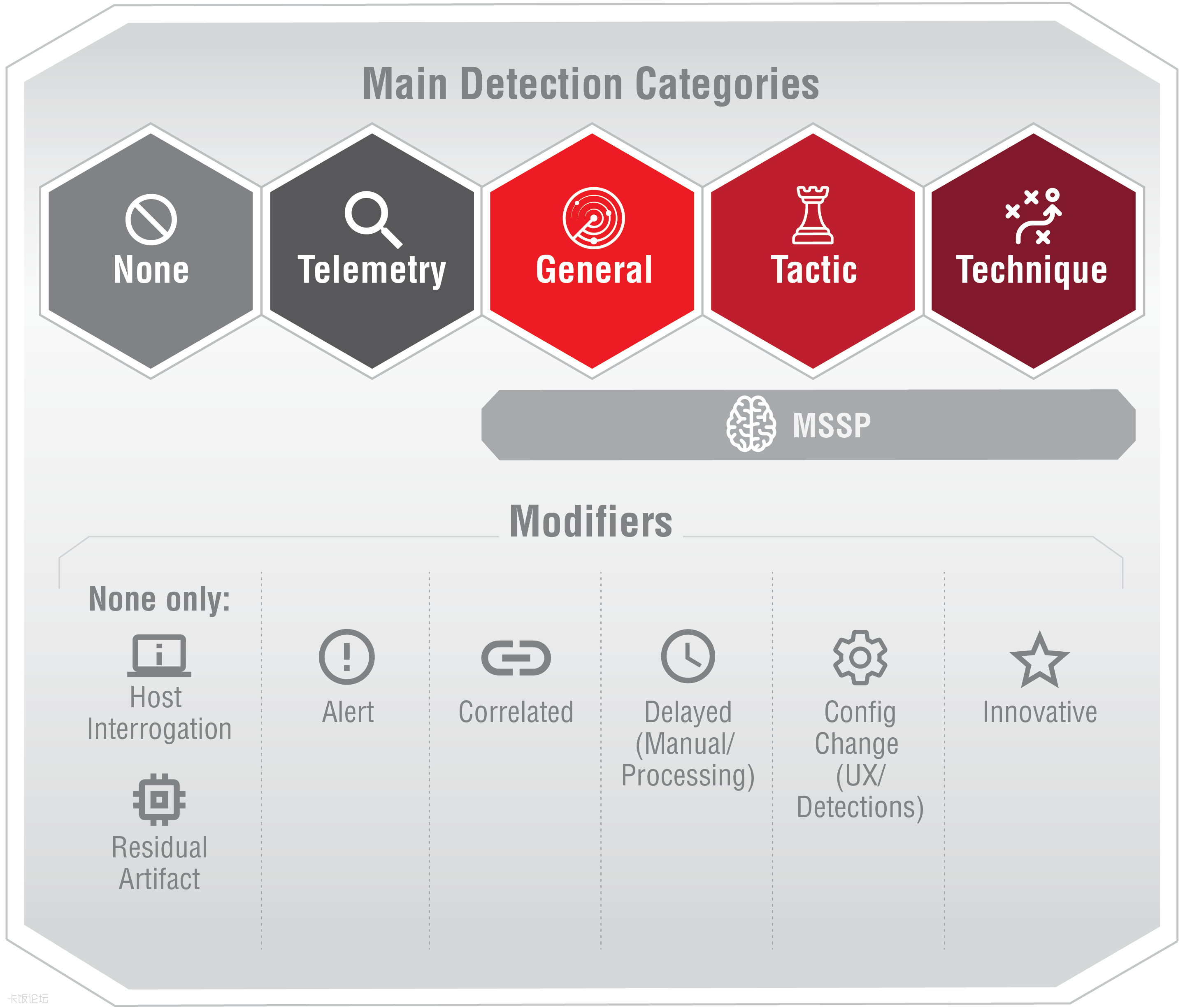
Environment:
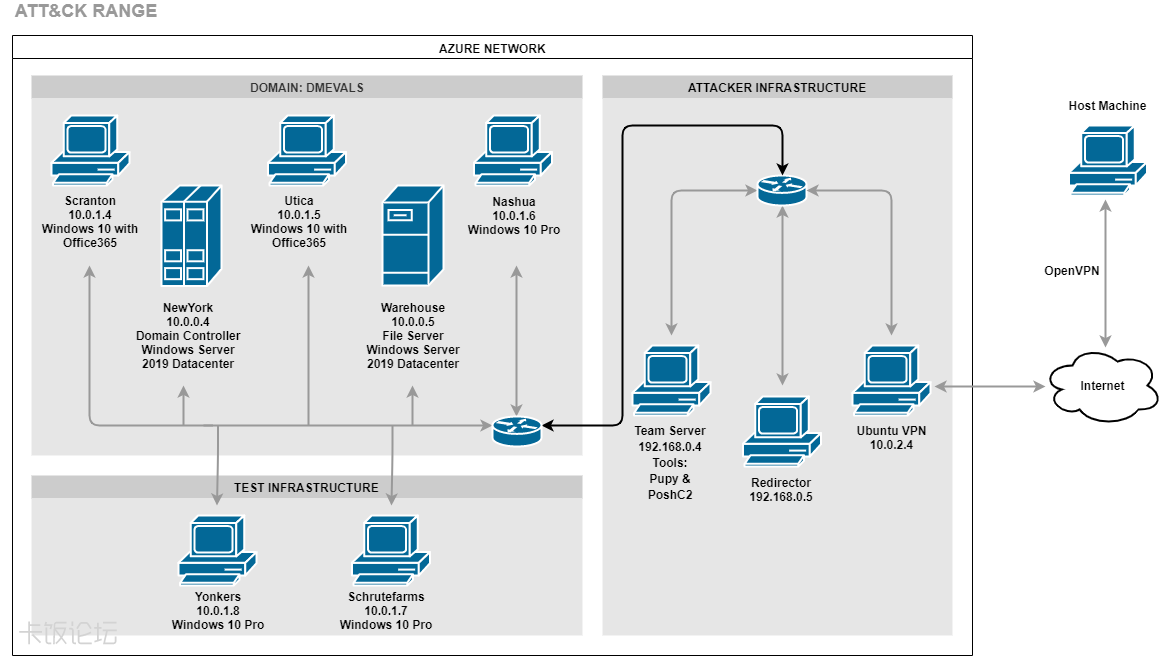
Technique Scope:

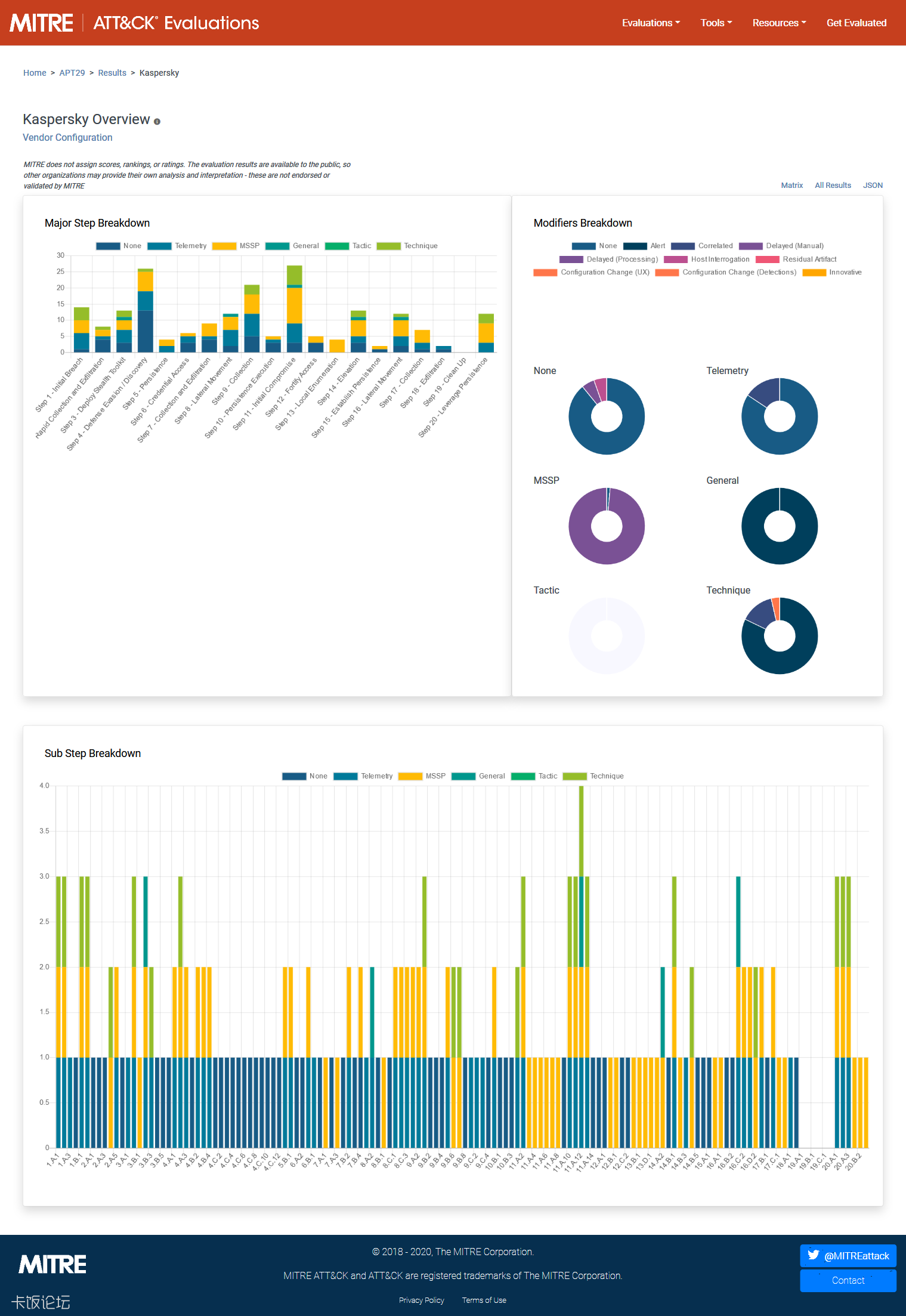
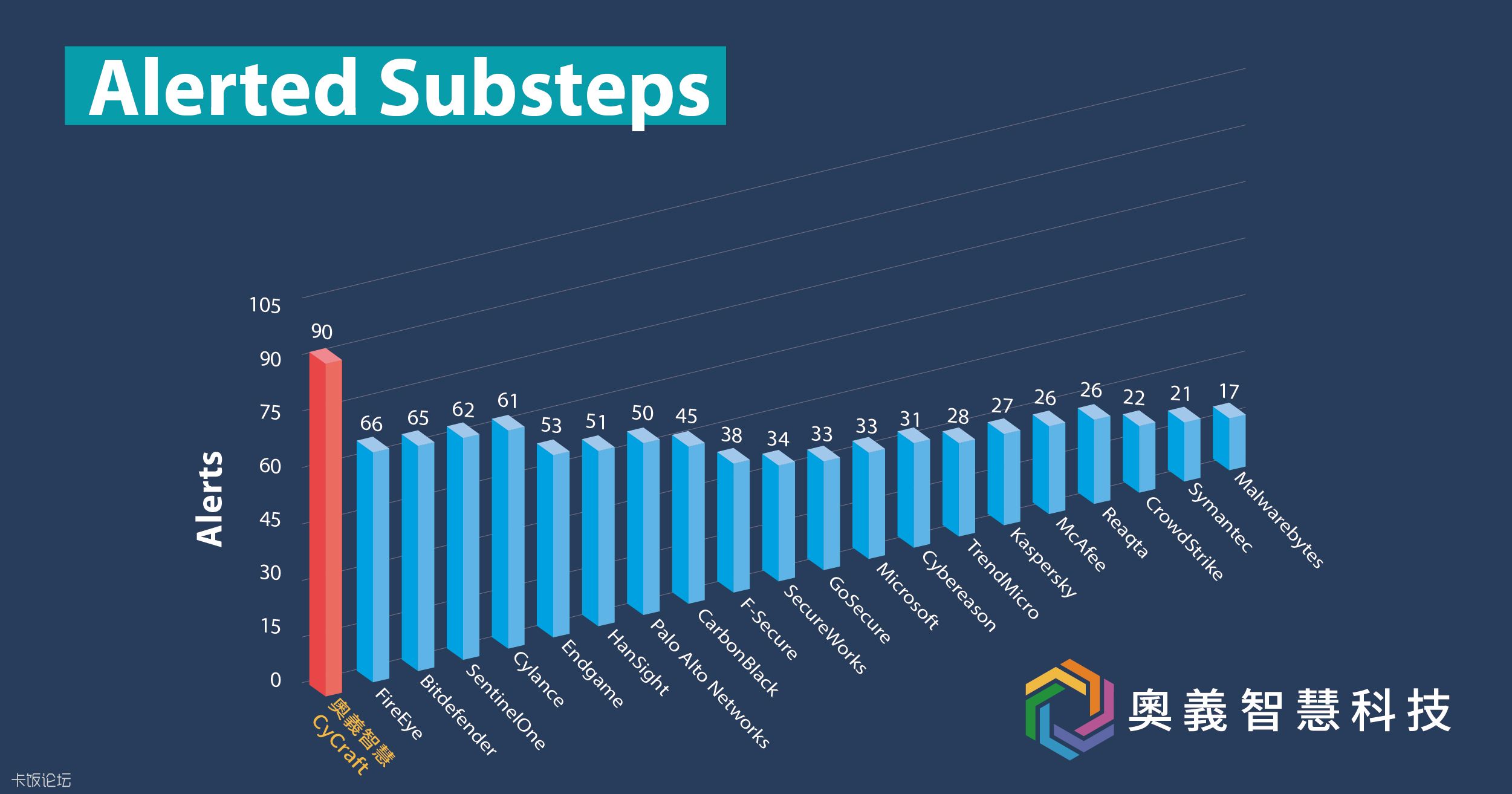
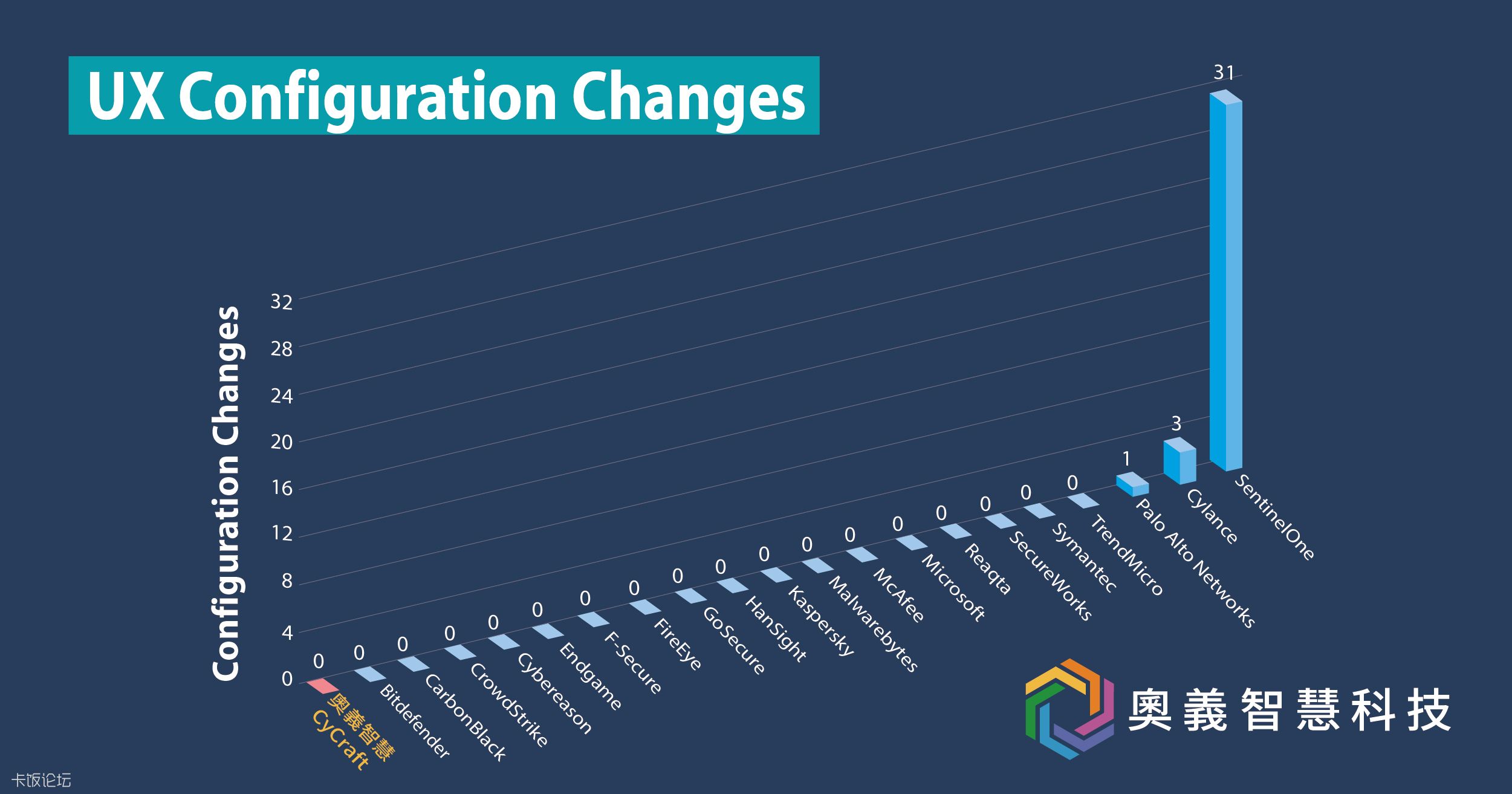
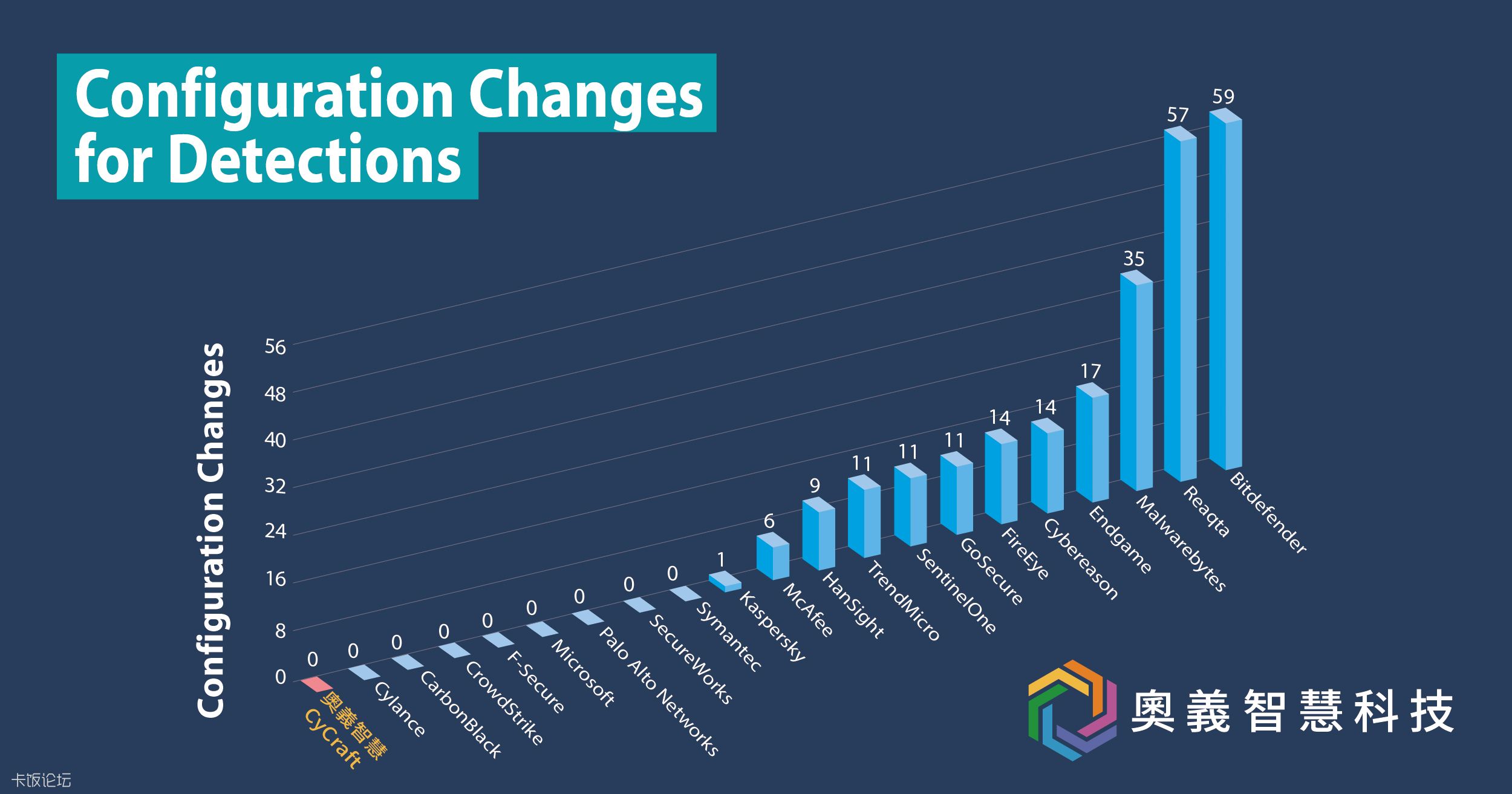
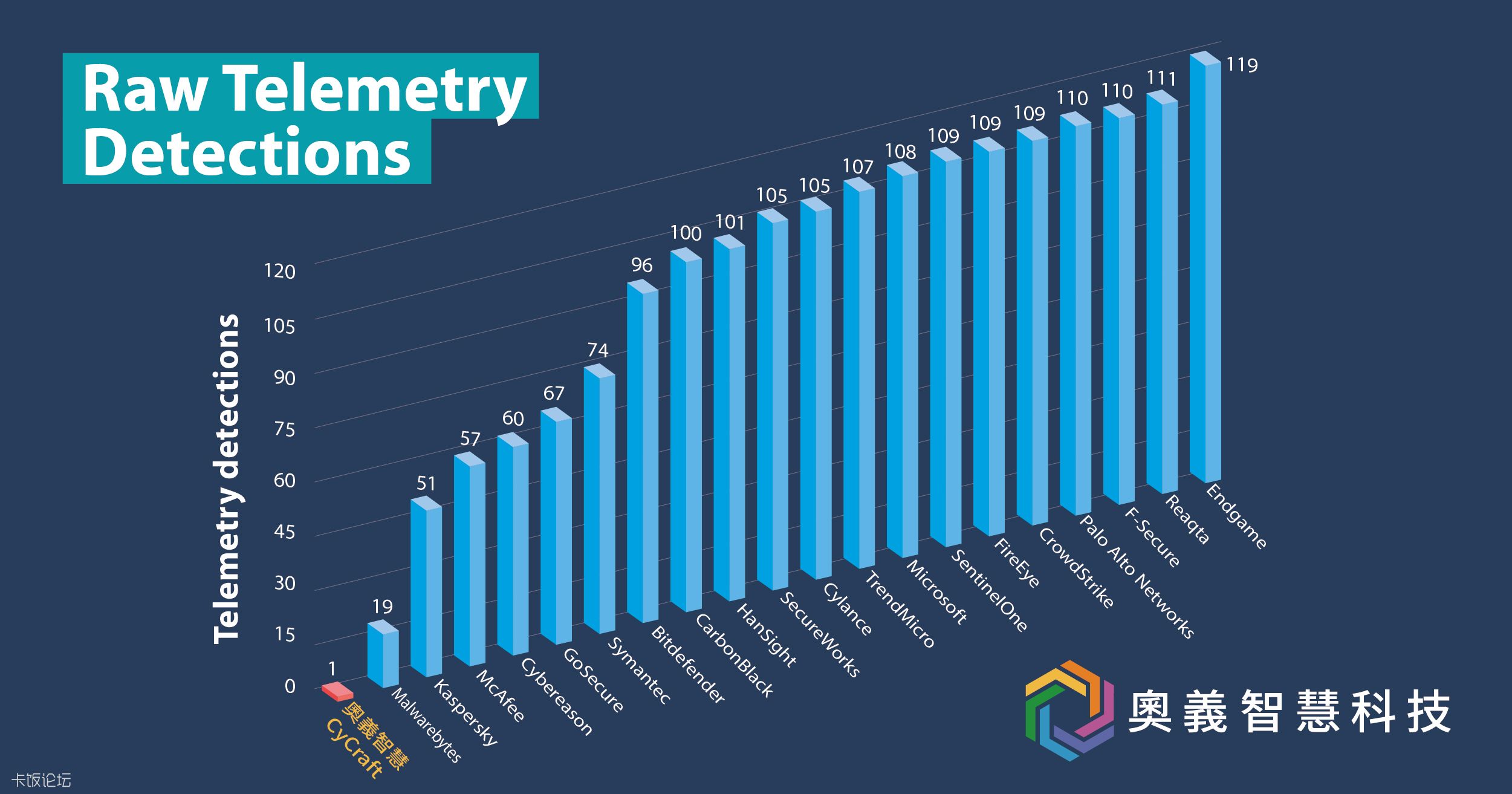
Every Participant has following evaluation results.
All Results
Matrix

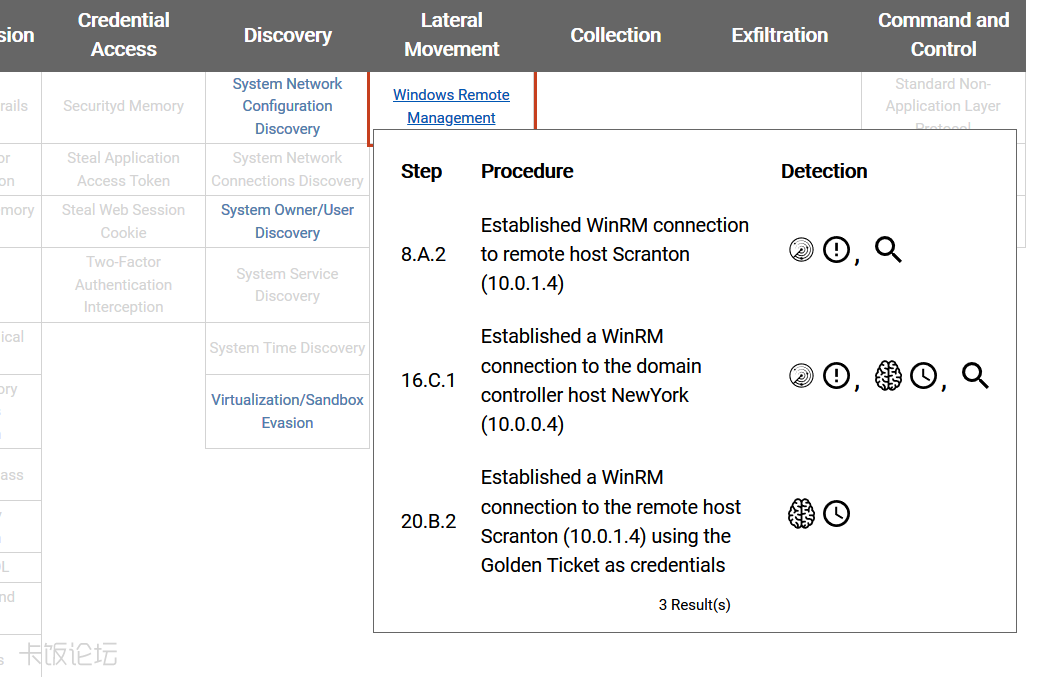
Configuration
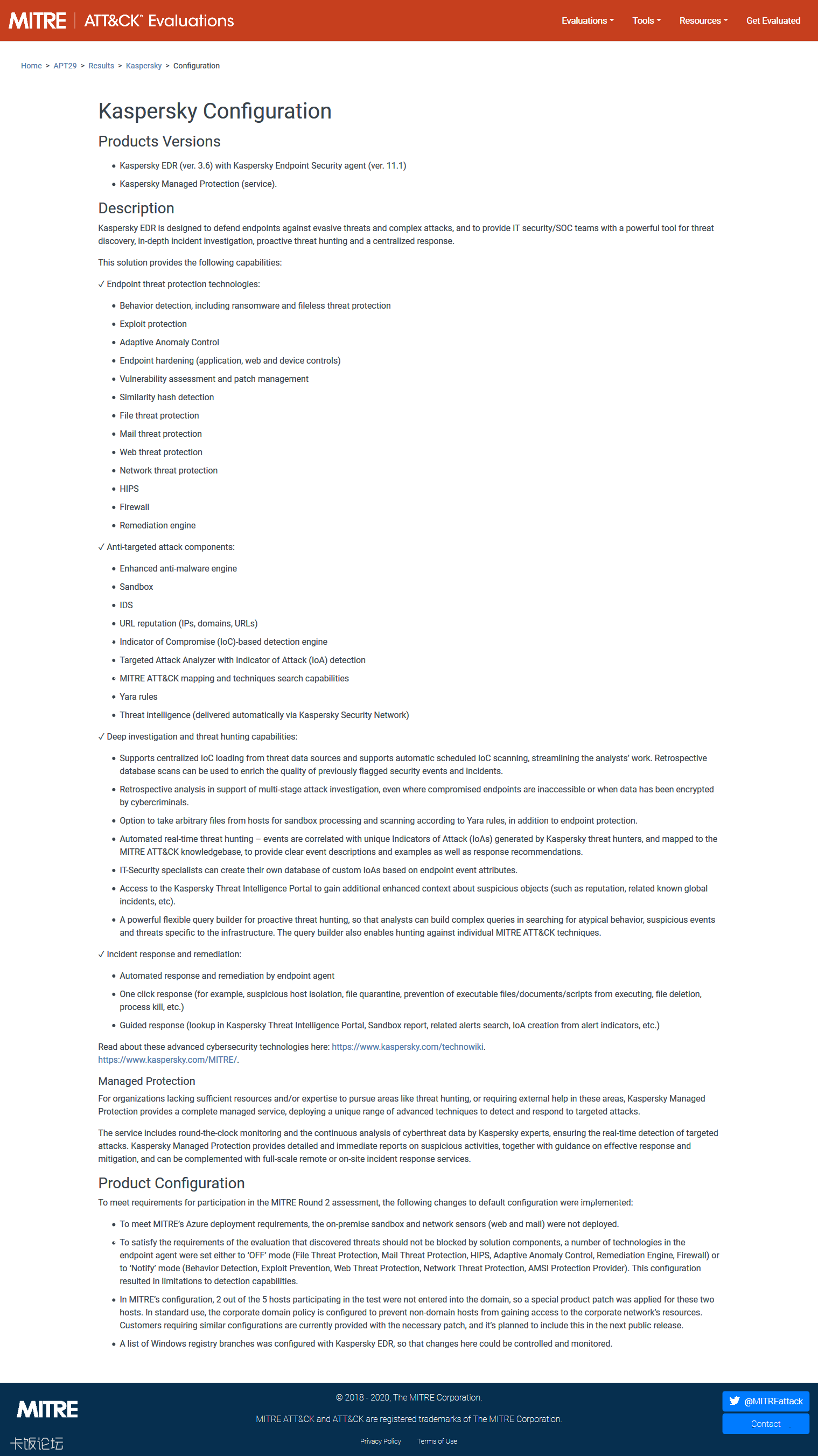
MITRE does not assign scores, rankings, or ratings. So we get these summary from the participants' websites.
https://www.fireeye.com/blog/products-and-services/2020/04/mitre-evaluation-demonstrates-endpoint-security-managed-defense-detection-leadership.html
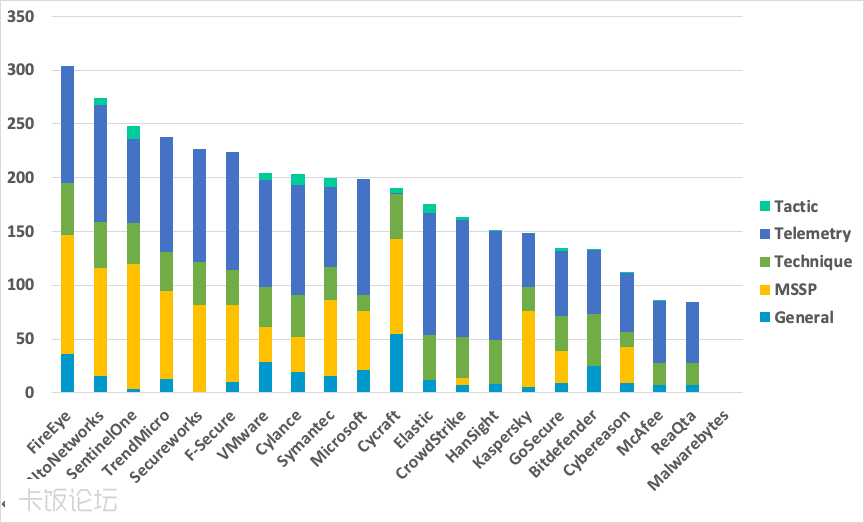
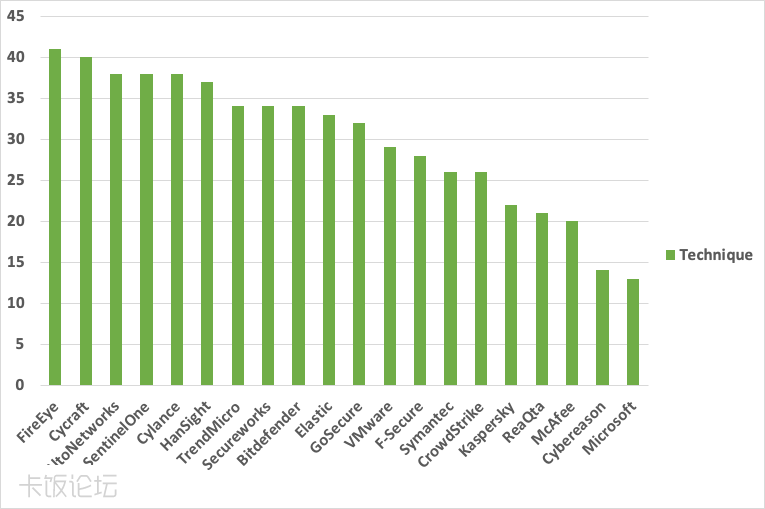
https://blog.paloaltonetworks.com/2020/04/cortex-mitre/
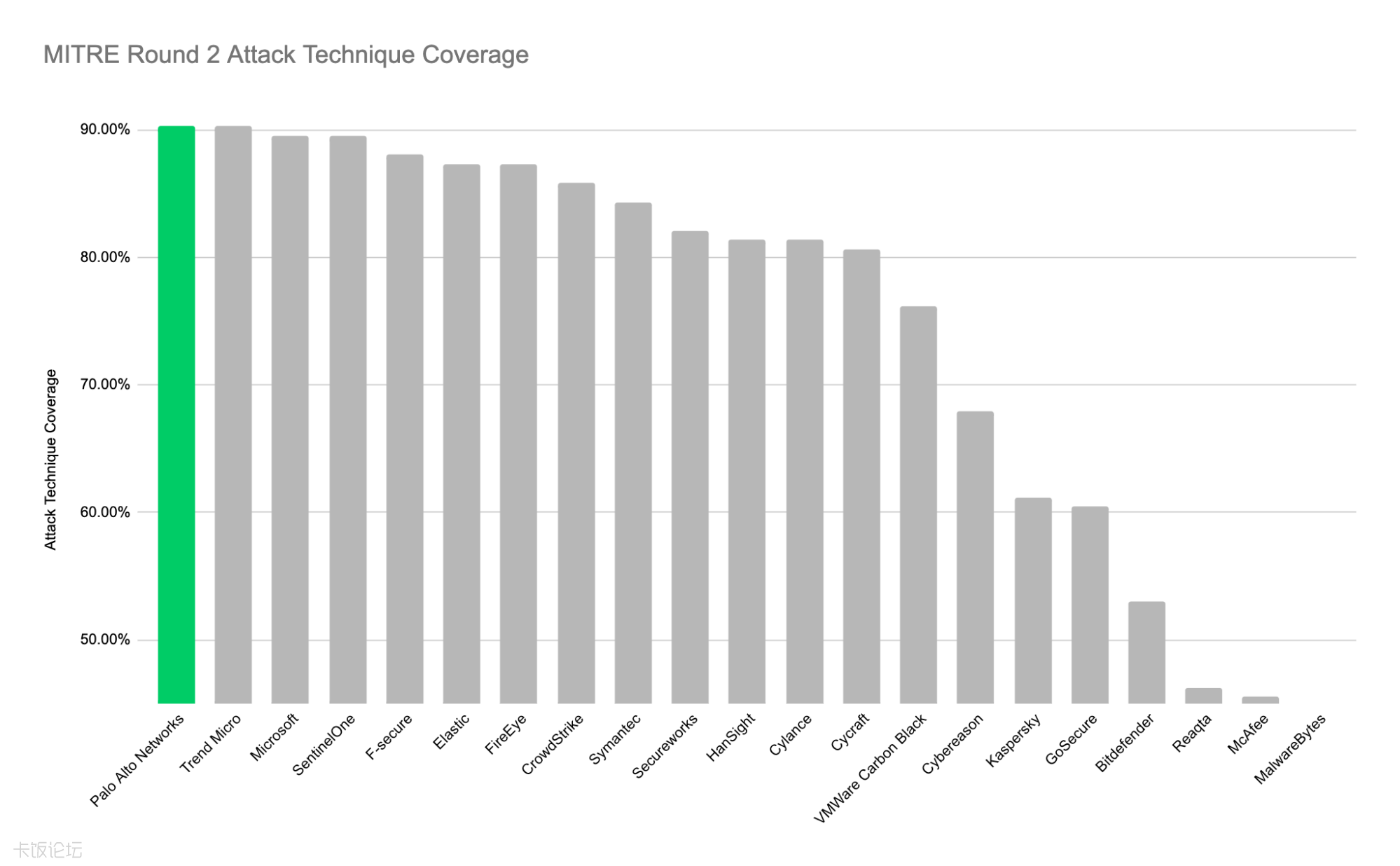
https://www.cycarrier.com/press_20200422.html
|