本帖最后由 petr0vic 于 2021-2-25 01:57 编辑
Over the past few months, Minerva Labs’ research team has received multiple alerts of possibly malicious code-unpacking from an executable named FlashHelperService.exe. We decided to investigate this binary in order to determine whether this is a false positive or actual malware. It appears that the binary exhibits various malicious techniques. Hence, we chose to publish our findings, in hopes of benefiting the community and helping others that are investigating the same case.
It is important to mention that the file is signed by “Zhong Cheng Network” which is a distributor of Adobe’s software in China. There are already numerous complaints on Adobe’s site about the company and its fishy software.
Analysis of the Binary:
The binary contains an embedded DLL encrypted inside its data section, which is reflectively loaded and executed:
Analysis of the Binary: The binary contains an embedded DLL encrypted inside its data section, which is reflectively loaded and executed:
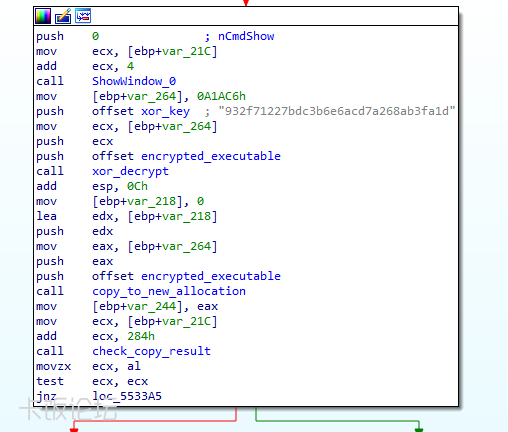
The in-memory DLL is internally named ServiceMemTask.dll and has numerous incriminating features: - A capability to access the flash[.]cn website and download files.
- Downloading encrypted DLL files from the same website, decrypting them, and reflectively loading them.
- Clear text names of various analysis tools are present inside the decrypted binary (which we did not see being used):
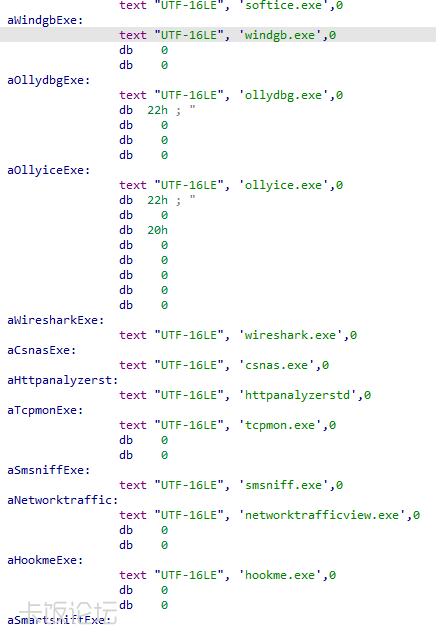
- An ability to profile the OS and send it back to the server.
The memory payload contacts the hardcoded URL hxxps://cloud.flash[.]cn/fw/cz/y0fhk8csvhigbzqy9zbv7vfzxdcllqf2.dcb and XOR decrypts data downloaded from there using the hardcoded key “932f71227bdc3b6e6acd7a268ab3fa1d”. The output is an obfuscated json file that serves as a task from the server:
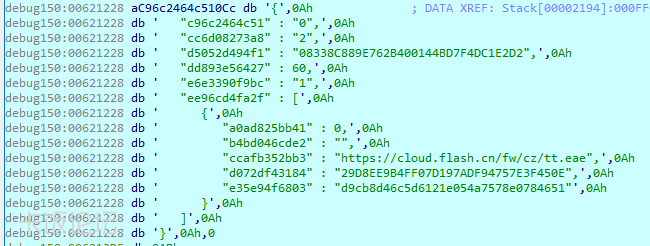
- ccafb352bb3 is the URL for the next payload.
- d072df43184 is the MD5 sum of the encrypted payload.
- e35e94f6803 is the 3DES key of the payload.
The DLL file is linked against curl, which it uses to download the file “tt.eae” into the modules main directory “C:\Users\Username\AppData\LocalLow\Adobe{过}{滤}Flash\FlashCfg”. The file is encrypted using 3DES, with an implementation similar to the one found here. After decryption and decompression (7zip) a PE file internally named "tt.dll" is revealed. The DLL file is yet again reflectively loaded and executed.
In order to determine how common this service is, we downloaded the official flash installation from flash.cn, which is signed by adobe:
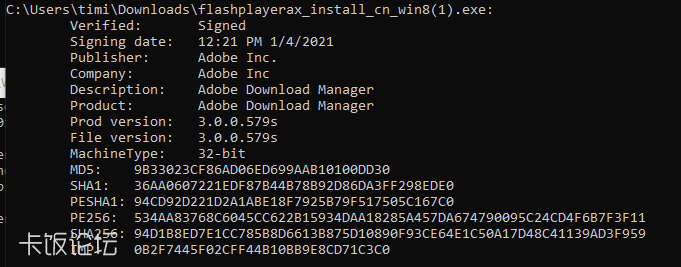
]After installing flash using this binary, the exact service (sha256: 8cb8e8c9fafa230ecf2f9513117f7679409e6fd5a94de383a8bc49fb9cdd1ba4) was installed on our machine. Addiotionally, Cisco’s Talos Intelligence have listed FlashHelperService.exe as one of the most prevalent threats in the third week of January 2021. After further reverse engineering, we managed to download and decrypt the popup producing binary, internally named “nt.dll”, that is loaded into FlashHelperService. The binary will open the browser with an annoying popup in predetermine timestamps. An example popup:
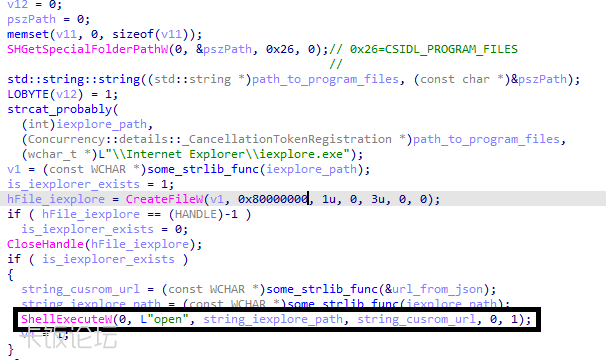
The code uses the Windows API function ShellExecuteW to open internet explorer with a URL fetched from another encrypted json:
Conclusion: This flexible binary execution framework seems redundant for a service that claims to update flash player. This is highly concerning, especially considering how widespread this binary is. After investigating its subsequent payload, we can determine that its final intent is adware-like. This functionality can be seen in the file “nt.dll”. This threat is especially concerning for two reasons: - The general binary distribution framework described in the blog could be used by an attacker to load malicious code, effectively bypassing traditional AVs disk signature check.
- Most enterprises with a Chinese office had this service installed in their organizational network. If this framework was used with a malicious intent, an attacker will have an initial foothold in many organizations.
IOCs: Hashes: 8cb8e8c9fafa230ecf2f9513117f7679409e6fd5a94de383a8bc49fb9cdd1ba4 (FlashHelperService.exe) d51100ae4f9e972b5582a129c6756df494be3d18a6824d2ca125158a8ac29f2a (ServiceMemTask.dll) 9b9e8e6ae50774d27472c63d64bc7daeeac8bea05b6b3c3025fbaae12366e214 (tt.dll)
0916BA911B2B5FABAFE02EC5E5032CBA548B01E7F081CC20E3D28A6634FB56CB (nt.dll)
URLs: - https://cloud.flash[.]cn/fw/cz/y0fhk8csvhigbzqy9zbv7vfzxdcllqf2.dcb - (tt.eae task)
- https://cloud.flash[.]cn/fw/cz/dc8c6538c49b02a2b08617aae1cc6991.dcb
- https://cloud.flash[.]cn/fw/cz/tt.eae
- https://cloud.flash[.]cn/fw/cz/nt.eae
https://blog.minerva-labs.com/the-curious-case-of-flashhelperservice-0
|